Add Authentication Security to Automotive End Points Using a Single Pin
Increasing electronic content on vehicles presents expanded attack surfaces to hackers. Digital authentication can reduce the risk of theft and counterfeiting of genuine and approved high-quality components.
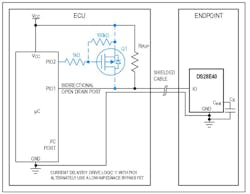
In mission-critical automotive applications such as ADAS and EV batteries, low-quality counterfeits can introduce safety risks if their performance is degraded compared with genuine components. Stolen components may not be calibrated to operate properly in a different vehicle. By adding a single authentication IC, you can now authenticate a component with only one signal between an electronic control unit (ECU) and end-point component (see figure).
Traditional approaches to component security and authentication use a secure microcontroller or even an automotive hardware security module (HSM). While a robust solution, this is costly and involves many electrical contacts from the host controller, significant printed-circuit-board (PCB) area, and extensive software development and verification to prevent bugs. Now, by adding just one compact, fixed-function IC, the end point can be secured by running only one signal plus ground reference in a shielded cable between ECU and end point.
The DS28E40, developed by Maxim Integrated, implements the 1-Wire protocol, which uses half-duplex communication and harvests power for the device parasitically through the communication line, thus reducing the need for a dedicated power line in the cable. Harvested energy is stored in an external capacitor.
Most automotive ECUs include a high-performance microcontroller; only one open-drain PIO pin with a pullup resistor is required for bidirectional communication. Security algorithm computations require up to 16 mA, beyond the pullup’s sourcing ability. If PIO1 can switch between the open drain and push/pull configuration with sufficient current sourcing, then it’s able to drive logic 1 during computations. Alternately, a low-impedance bypass FET can be added and controlled by PIO2 to deliver sufficient current.
The device employs the Elliptic Curve Digital Signal Algorithm (ECDSA) public-key security algorithm. Library and code examples are available to easily implement the security layer on the ECU host processor.
With this asymmetric security algorithm, key management is simplified by allowing the host to directly read the unique public key from the DS28E40. Then the host can issue random challenge messages to the DS28E40, which digitally signs the challenge with its internal private key that’s never exposed to the outside world. If the host verifies that the signature matches the public key, then the automotive end point can be trusted by the ECU.
References
Video: Introduction to the DS28E40 Deep Cover Automotive 1-Wire Authenticator