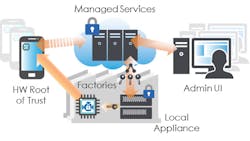
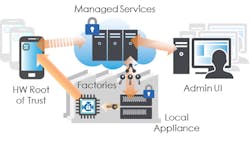
The CryptoManager technology approach addresses all aspects of design and deployment including:
- SoC security
- Supply chain security
- Device and application security
- Network and device lifecycle
SoC security provides the root of trust. It is a microcontroller that is implemented as part of the SoC to manage and secure the keys used for secure boot and service authentication. It can control debug modes to prevent reverse engineering. It also provides chip authentication thereby preventing counterfeiting. It also manages the one-time-programming (OTP) of on-chip resources.
The supply chain security allows devices to be built anywhere. An on-site CryptoManager Security Appliance it part of the manufacturing process providing secure SoCs with their initial keys. It provides audit management, device configuration, key management and personalization support.
The device and application security starts with the secure boot of an operating system. It can then provide a secure repository for authentication and authorization supporting digital rights management (DRM) like HDCP (High-bandwidth Digital Content Protection) as well as services like VPNs.
The network and device lifecycle includes support services such as device provisioning, subscription management, secure payments, device authorization and RMA/test support.
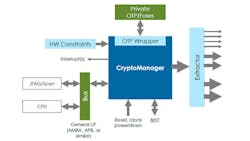
The design of an SoC is where a CryptoManager security engine (Fig. 2) is added to the mix. It is a microcontroller that incorporates measures to prevent access to the secure keys that it stores and manages. It provides secure boot support for the host CPU. This microcontroller manages the on-chip OTP fuses that can be used to customize a system. It can also control the JTAG interface.
The extractor interface provides access to custom SoC services. It allows the CryptoManager security engine to enable or disable services.
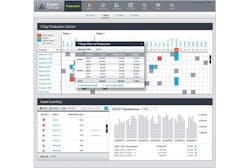
The CryptoManager infrastructure is just as important as the CryptoManager security engine. It includes the CryptoManager Security Appliance and the cloud-based CryptoManager Control Center (Fig. 3). The control center tracks and manages all security changes from the initial programming of a chip with security keys to in-field modification.
The CryptoManager Security Appliance is essentially a black box that provides a communication data stream to a CryptoManager security engine. These transactions can monitor or manage features on the SoC. All this is logged and managed by the control center. The contents of a CryptoManager security engine cannot be changed without involving the security appliance and control center.
The CryptoManager Control Center is set up to securely manage multiple factories. These may be manufacturing the same or different SoCs that incorporate the CryptoManager security engine. Each has at least one of the appliances on-site. The system has a hierarchical architecture allowing different companies to manage different aspects of manufacturing and deployment. For example, a company may create the SoCs but these are then handed off to an OEM and final devices are sold to service providers that deliver them to their customers. Each of the organizations could have their own CryptoManager Control Center interface so each can manage their own keys on a device.
A manufacturer could enable services or peripherals on a device using this methodology. Service providers would be able to do the same for devices in the field using network communication. They would only be able to change services and settings they have been given rights to so a service provider would be unable to enable services or peripherals that the manufacturer had placed limits on.
This approach allows any vendor in the chain to minimize the number of SKUs since devices will be identical except for the keys programmed into the system.
The technology can support any platform so it is suitable for everything from Android and Windows to iOS.
The use of CryptoManager technology requires a major commitment at least from the initial SoC design and manufacturing. It does offer some compelling features. At this point, RAMBUS provides the cloud-based control center support and the CryptoManager Security Appliances.
About the Author
William G. Wong
Senior Content Director - Electronic Design and Microwaves & RF
I am Editor of Electronic Design focusing on embedded, software, and systems. As Senior Content Director, I also manage Microwaves & RF and I work with a great team of editors to provide engineers, programmers, developers and technical managers with interesting and useful articles and videos on a regular basis. Check out our free newsletters to see the latest content.
You can send press releases for new products for possible coverage on the website. I am also interested in receiving contributed articles for publishing on our website. Use our template and send to me along with a signed release form.
Check out my blog, AltEmbedded on Electronic Design, as well as his latest articles on this site that are listed below.
You can visit my social media via these links:
- AltEmbedded on Electronic Design
- Bill Wong on Facebook
- @AltEmbedded on Twitter
- Bill Wong on LinkedIn
I earned a Bachelor of Electrical Engineering at the Georgia Institute of Technology and a Masters in Computer Science from Rutgers University. I still do a bit of programming using everything from C and C++ to Rust and Ada/SPARK. I do a bit of PHP programming for Drupal websites. I have posted a few Drupal modules.
I still get a hand on software and electronic hardware. Some of this can be found on our Kit Close-Up video series. You can also see me on many of our TechXchange Talk videos. I am interested in a range of projects from robotics to artificial intelligence.