Security-Oblivious Design Makes TrustZone Vulnerable to Attack (.PDF Download)
Creating advanced driver-assistance systems (ADAS) and self-driving cars is a substantial technical challenge. Securing these designs is also challenging, but security hardware can make this task much easier—if it works.
Typically, the root of trust starts in hardware with keys that must be protected and security hardware that provides secure boot support. ARM’s TrustZone is one implementation that provides this support. TrustZone technology is at the center of ARM’’s security message, so compromising this system would have a significant impact on automotive security.
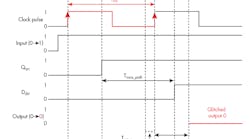
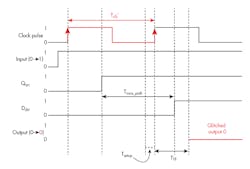
On that front, researchers at Columbia University succeeded in attacking a security-oblivious design of a TrustZone-based ARM system-on-chip (SoC) implementation by compromising the Dynamic Voltage and Frequency Scaling (DVFS) support (Fig. 1). Adrian Tang, Simha Sethumadhavan, and Salvatore Stolfo presented their paper, CLKSCREW: Exposing the Perils of Security-Oblivious Energy Management, at the 26th USENIX Security Symposium in Vancouver, BC, Canada.
1. Columbia University researchers were able to use the Dynamic Voltage and Frequency Scaling (DVFS) support to induce bit-level faults due to overclocking.