Secure Control FPGA Packs Post-Quantum Protections
Future quantum computers could unravel modern cryptography. Lattice Semiconductor is trying to stay a step ahead of them with its first family of FPGAs to run the latest post-quantum cryptography algorithms.
Small, low-power FPGAs such as Lattice’s Nexus family are widely used to bring hardware-based security to data centers and telecom, industrial, automotive, and aerospace and defense systems. They also come with a hardware root of trust (RoT) that serves as the secure anchor for the system.
The RoT makes sure everything from hardware to the software is what it says it is, and nothing has been compromised. One of its main functions is ensuring a secure boot of the system before shifting to prevent attacks and protecting data during runtime.
The chips are also increasingly used to run advanced cryptography algorithms that underpin it all. However, they have largely been limited to supporting pre-quantum cryptography schemes such as the Rivest-Shamir-Adleman (RSA) cryptosystem and error correction code (ECC).
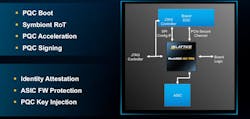
The MachX05-NX TDQ adds the ability to run cryptographic algorithms that can block attacks from quantum computers. Lattice said the Nexus FPGA runs all of the algorithms in the Commercial National Security Algorithm (CNSA 2.0) standard, including ML-DSA, ML-KEM, LMS, XMSS, and AES256, and uses them for cryptographic operations such as encryption, decryption, and digital signatures (Fig. 1). It applies the programmable logic in the FPGA to accelerate them in hardware instead of running software that can overtax general-purpose MCUs.
The company said it packed these post-quantum protections into a single chip with 55K logic cells and a maximum power of 5 W. It also supports the same pre-quantum cryptography algorithms as its predecessor — the MachX05-NX.
“We're bringing PQC to the masses,” said Mamta Gupta, AVP of strategic business development for security at Lattice. “We differentiate because we thought of it from the ground up. We didn’t retrofit it. We already have hardened asymmetric and symmetric cryptography in there and then we add the PQC on top of it, which is also cryptographically hardened in these devices.”
It also features a unique “crypto-agile” architecture that enables secure updates of the PQC algorithms in the field, keeping pace with future vulnerabilities.
Lattice, which released the PQC-ready FPGAs at the Open Compute Project (OCP) Global Summit in San Jose, is already shipping them to leading customers in the communications and data center markets.
Race Against Time: The Urgency of Post-Quantum Cryptography
Most experts agree that large-scale quantum computers are still at least a decade away at this point. But as it moves out of the concept phase, the risks to traditional cryptography are coming into focus, said Gupta.
The concern is that quantum computers, if a large enough one is ever built, could break the cryptography algorithms used to secure virtually every device today and protect the data inside from attackers. The most widely used are RSA and ECC. They’re the bedrock of public-key cryptography, which uses a pair of keys linked by very complex mathematics — a public key and a private key — to encrypt and decrypt data and then verify its integrity. Even the current state-of-the-art in asymmetric cryptography, RSA-2048, could be compromised.
Even though these large-scale code breakers are likely more than a decade out, the threat isn’t limited to the future. One of the risks is the rise of “harvest now, decrypt later” (HNDL) attacks, where hackers steal and store encrypted data with the intent to decrypt it in the future when quantum computers are powerful enough.
>>Check out more coverage of the 2025 OCP Global Summit
“All data today is being secured by traditional cryptography, and whenever attackers have access to quantum computers, that will be like paper to a bullet,” said Gupta.
To stay ahead of the threat, technology giants and other companies are taking steps to shift to post-quantum cryptography (PQC). It replaces vulnerable algorithms such as RSA and ECC with lattice- and hash-based alternatives that are too complex for quantum computing to unravel. On top of that, regulators around the world are trying to stay on top of things. About a year ago, the National Institute of Standards and Technology (NIST) released the first industry standards for PQC algorithms.
The commercial cybersecurity unit of the NSA has also rolled out CNSA 2.0, a set of post-quantum algorithms (noted above) set to replace current standards used by the U.S. government for securing devices and data inside them. The CSNA 2.0 standard will require all national security system owners, operators, and vendors to adopt PQC in all new software by 2025. All currently deployed software must be transitioned by 2030 with full adoption in 2035.
A Secure FPGA That Supports Pre- and Post-Quantum Cryptography
Lattice said its latest Nexus-based FPGA is specifically designed to ease the transition to PQC technology.
The flash-based FPGAs run a wide range of pre-quantum (including symmetric and asymmetric standards such as AES-CBC/GCM 256-bit, ECDSA-384/521, SHA-384/512, and RSA-3072/4096) and post-quantum algorithms (including ML-DSA, ML-KEM, LMS, XMSS, AES-256, SHA2, SHA3, and SHAKE). They can be used to protect everything from the device itself to the larger system to sensitive data. Their hardware-enforced RoT with integrated flash enables instant-on, single-chip secure boot, preventing malicious code from running.
In data centers, Lattice said FPGAs are often used in AI server motherboards, in roles ranging from secure control modules (SCMs) and host processor modules (HPMs) to network interface cards (NICs), to help prevent threats that can bypass traditional software defenses.
FPGAs are comprised of a programmable fabric of logic and on-chip memory that can be rearranged to enable hardware acceleration of specific algorithms such as PQC. This gives them the real-time performance that can be the difference between blocking hackers and them slipping through the security.
FPGAs are also field-programmable, which provides more flexibility than custom silicon in an era of evolving threats. Companies are able to adapt and update the underlying cryptography and other security technologies.
However, the flexibility of FPGAs can also be used against it, leveraged by hackers to access everything from the hardware, software, firmware, and data on the device or steal the cryptographic keys used to protect it all. As a result, it’s important to secure the FPGA as rigorously as the systems protected by it. For instance, the TDQ FPGAs can use post-quantum cryptography to secure the code — called the bitstream — used to program the programmable logic of the FPGA as well as authenticate it.
The company said the FPGA is being used both as the primary RoT and as a helper RoT. The FPGA provides post-quantum protection for the system while a main board controller manages the pre-quantum cryptography (Fig. 2).
Then the FPGA can run the PQC, including ML-KEM for sharing secret keys to the main board controller, ML-DSA for creating digital signatures, and LMS and XMSS for authenticating that the software and firmware is safe before it’s loaded into the system processor. It can also use PQC to facilitate a secure boot.
“The entire board suddenly becomes PQC protected,” said Ramya Chandrasekaran, senior manager of product management and marketing at Lattice. “We can act as the primary root of trust, or we can act as a helper root of trust. We work on both sides, and so we’re being adopted in both ways,” she said, adding that this presents a relatively easy way to add post-quantum protection to data centers that do not already have it.
Instead of replacing every single pre-quantum algorithm with largely untested post-quantum ones, the FPGAs can run both at the same time, adding more levels of protection and easing integration into systems. The chips also support secure key management with revokable root keys and a robust key hierarchy, allowing many pre- and post-quantum public keys to be stored and deployed in systems at the same time, said Chandrasekaran.
The MachX05-NX TDQ: A Semi-Hardened Secure Control FPGA
Lattice said it’s trying to differentiate itself by bringing all of these algorithms into a family of low-power FPGAs.
The underlying architecture of the MachX05-NX TDQ is all about performance-per-watt, said Lattice. But it also semi-hardened — or “cryptographically hardened,” as the company called it — PQC into the programmable logic and on-chip memory within the FPGA.
“We have all the symmetric and asymmetric cryptography hardened on the silicon, and then we have taken the PQC algorithms, and we have cryptographically hardened them, and we put them into the device,” said Gupta. “Users cannot change them. Users cannot even touch them.”
Even though it lacks the advantages of a fully hardened ASIC, Lattice said its semi-hard FPGA can run the computationally intense operations at the heart of PQC with less latency and lower power than running them on a general-purpose MCU or hardware security module (HSM), which often add significant overhead with PQC. Its cryptographic hardening is unique — and how it works is proprietary. But the company explained that the approach strikes a balance: strong baked-in security without sacrificing the flexibility required to stay ahead of hackers.
“Other companies are implementing or accelerating it in software, so they are offering it on battle tanks — very sophisticated SoC-class devices — because they need the performance to run these algorithms,” said Gupta. “We’re not forcing you to use a device that consumes 15 to 20 W of power because you need a huge SoC to run all these algorithms in software. The maximum power of the new device is less than 5 W, and depending on the application, we can come in under 3 W. So that's where our differentiation is coming from.”
The first chip in the MachX05-NX FPGA family features up to 55K logic cells to run the complete set of algorithms under the CNSA standard, but the company plans to scale the family up to 96K logic cells in the future (Fig. 3). The FPGA is supplemented by up to 300 robust programmable I/Os and 15 MB of integrated flash, which is important because post-quantum keys are many times larger than pre-quantum cryptographic keys and they must be stored somewhere. Lattice also released smaller FPGAs with 20K and 30K logic cells that can only run one or two CNSA algorithms at a time, said Chandrasekaran.
While future versions of these algorithms could be locked into a hardware RoT or hardened in IP blocks within a board controller, Gupta noted that these chips are too rigid to stay ahead of new threats. FPGAs have the ability to update cryptographic protections directly in hardware — without replacing the chip. That is critical in the context of post-quantum cryptography, where the algorithms are constantly changing.
“Nobody wants to harden these algorithms yet because they can change,” said Gupta. “They're not battle tested; they’re still evolving.”
To address that uncertainty, Lattice integrates what it calls “crypto agility” into its devices. The patent-pending technology gives it the ability to update and upgrade the “cryptographically hardened” algorithms in the FPGA while it remains in the field.
The company is leveraging the fact that its FPGAs have flexible locking. The chips have a mode where customers are able to permanently lock everyone out, and then nobody can update anything on it. But its customers can also use another mode that enables secure remote unlocking and updating without removing the device from the data center or other systems.
In such cases, Lattice said it can use the crypto-agility technology to securely access the device and load more advanced PQC or other cryptographic algorithms into it wirelessly.
“So, we're future-proofing ourselves, too,” said Chandrasekaran.
>>Check out more coverage of the 2025 OCP Global Summit
About the Author
James Morra
Senior Editor
James Morra is the senior editor for Electronic Design, covering the semiconductor industry and new technology trends, with a focus on power electronics and power management. He also reports on the business behind electrical engineering, including the electronics supply chain. He joined Electronic Design in 2015 and is based in Chicago, Illinois.