What’s The Difference Between The OSI Seven-Layer Network Model And TCP/IP?
Download the PDF of this article.
Whether it’s wired or wireless, most data communications today happens by way of packets of information travelling over one or more networks. But before these networks can work together, though, they must use a common protocol, or a set of rules for transmitting and receiving these packets of data. Many protocols have been developed. One of the most widely used is the Transmission Control Protocol/Internet Protocol (TCP/IP). Also, a generic protocol model used in describing network communications known as the Open System Interconnection (OSI) model from the International Organization for Standardization (ISO) is useful for comparing and contrasting different protocols.
The OSI Model
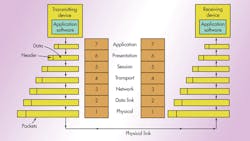
Designated ISO/IEC 7498-1, the OSI model is a standard of the International Organization for Standardization (ISO). It is a general-purpose paradigm for discussing or describing how computers communicate with one another over a network. Its seven-layered approach to data transmission divides the many operations up into specific related groups of actions at each layer (Fig. 1).
The transmitting computer software gives the data to be transmitted to the applications layer, where it is processed and passed from layer to layer down the stack with each layer performing its designated functions. The data is then transmitted over the physical layer of the network until the destination computer or another device receives it. At this point the data is passed up through the layers again, each layer performing its assigned operations until the data is used by the receiving computer’s software.
During transmission, each layer adds a header to the data that directs and identifies the packet. This process is called encapsulation. The header and data together form the data packet for the next layer that, in turn, adds its header and so on. The combined encapsulated packet is then transmitted and received. The receiving computer reverses the process, de-encapsulating the data at each layer with the header information directing the operations. Then, the application finally uses the data. The process is continued until all data is transmitted and received.
All of the necessary and desirable operations required are grouped together in a logical sequence at each of the layers. Each layer is responsible for specific functions:
• Layer 7 – application: This layer works with the application software to provide communications functions as required. It verifies the availability of a communications partner and the resources to support any data transfer. It also works with end applications such as domain name service (DNS), file transfer protocol (FTP), hypertext transfer protocol (HTTP), Internet message access protocol (IMAP), post office protocol (POP), simple mail transfer protocol (SMTP), Telnet, and terminal emulation.
• Layer 6 – presentation: This layer checks the data to ensure that it is compatible with the communications resources. It ensures compatibility between the data formats at the applications level and the lower levels. It also handles any needed data formatting or code conversion, as well as data compression and encryption.
• Layer 5 – session: Layer 5 software handles authentication and authorization functions. It also manages the connection between the two communicating devices, establishing a connection, maintaining the connection, and ultimately terminating it. This layer verifies that the data is delivered as well.
• Layer 4 – transport: This layer provides quality of service (QoS) functions and ensures the complete delivery of the data. The integrity of the data is guaranteed at this layer via error correction and similar functions.
• Layer 3 – network: The network layer handles packet routing via logical addressing and switching functions.
• Layer 2 – data link: Layer 2 operations package and unpack the data in frames.
• Layer 1 – physical: This layer defines the logic levels, data rate, physical media, and data conversion functions that make up the bit stream of packets from one device to another.
There are two key points to make about the OSI model. First, the OSI model is just that, a model. Its use is not mandated for networking, yet most protocols and systems adhere to it quite closely. It is mainly useful for discussing, describing, and understanding individual network functions.
Second, not all layers are used in some simpler applications. While layers 1, 2, and 3 are mandatory for any data transmission, the application may use some unique interface layer to the application instead of the usual upper layers of the model.
Some technologies, like Time Sensitive Networking (TSN), address a specific layer. In this case it is layer 2.
TCP/IP
TCP/IP was developed during the 1960s as part of the Department of Defense’s (DoD) Advanced Research Projects Agency (ARPA) effort to build a nationwide packet data network. It was first used in UNIX-based computers in universities and government installations. Today, it is the main protocol used in all Internet operations.
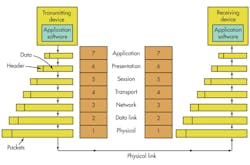
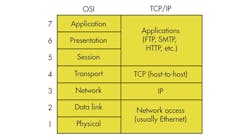
TCP/IP also is a layered protocol but does not use all of the OSI layers, though the layers are equivalent in operation and function (Fig. 2). The network access layer is equivalent to OSI layers 1 and 2. The Internet Protocol layer is comparable to layer 3 in the OSI model. The host-to-host layer is equivalent to OSI layer 4. These are the TCP and UDP (user datagram protocol) functions. Finally, the application layer is similar to OSI layers 5, 6, and 7 combined.
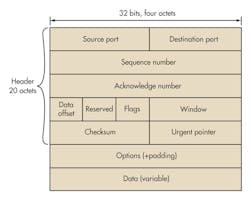
The TCP layer packages the data into packets. A header that’s added to the data includes source and destination addresses, a sequence number, an acknowledgment number, a check sum for error detection and correction, and some other information (Fig. 3). The header is 20 octets (octet = 8 bits) grouped in 32-bit increments. These bits are transmitted from left to right and top to bottom.
At the receiving end of the link, TCP reassembles the packets in the correct order and routes them up the stack to the application. TCP can retransmit a packet if an error occurs. In any case, TCP’s main job is just to pack and unpack the data and provide some assurance of the reliable transmission of error-free data. The IP layer actually transmits the TCP packet.
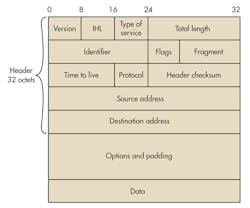
The IP layer transmits the data over the physical-layer connection. IP adds its own header to the packet (Fig. 4). The header comprises 32 octets again grouped in 32-bit words. Note the 32-bit source and destination addresses. These are the well-known IP addresses that we see in dotted decimal format (e.g., 197.45.204.36) where each 8-bit octet is expressed in its decimal value. This is the address assigned to the device by the Internet Assigned Numbers Authority (IANA).
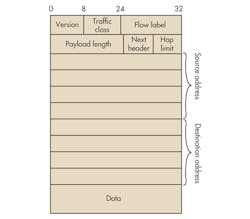
The header in Figure 4 is that used in IP version 4 (IPv4). Since the IANA has run out of 32-bit addresses (232 of them!), a newer version is rapidly being adopted. IPv6 uses 128-bit addresses (Fig. 5). With 2128 addresses, there should be enough for all of the planet’s computers, tablets, and smart phones as well as all of the devices that may be connected to form the so-called Internet of Things (IoT).
Once the IP header is added to the data, it is transferred to the Network Access layer. This layer repackages the data again into Ethernet packets or some other protocol for final physical transmission. The Ethernet packets are then reconfigured again for transmission over a DSL or cable TV connection or over a wide-area network using Sonet or optical transport network (OTN).
Summary
TCP/IP is the older of the two approaches to data communications and is well established throughout the world. The OSI model, however, is a proven concept that is used in all other data communications protocols. It will continue to be used as a guideline for all other communications applications.
References
- Frenzel, Louis E., Principles of Electronic Communication Systems, 3rd edition, McGraw Hill, 2008.
- Russell, Andrew, “The Internet That Wasn’t,” IEEE Spectrum, August 2013
- Stewart, Michael Stewart, Foundational Focus: OSI Mode –Breaking Down the Seven Layers, Global Knowledge Training LLC, 2013.
- Simoneau, Paul, The TCP/IP and OSI Models, Global Knowledge Training LLC, 2011.
About the Author

Lou Frenzel
Technical Contributing Editor
Lou Frenzel is a Contributing Technology Editor for Electronic Design Magazine where he writes articles and the blog Communique and other online material on the wireless, networking, and communications sectors. Lou interviews executives and engineers, attends conferences, and researches multiple areas. Lou has been writing in some capacity for ED since 2000.
Lou has 25+ years experience in the electronics industry as an engineer and manager. He has held VP level positions with Heathkit, McGraw Hill, and has 9 years of college teaching experience. Lou holds a bachelor’s degree from the University of Houston and a master’s degree from the University of Maryland. He is author of 28 books on computer and electronic subjects and lives in Bulverde, TX with his wife Joan. His website is www.loufrenzel.com.