Encryption is critical to network computer communication, secure storage, and a host of other security aspects to computing, including the Internet of Things (IoT). Encryption technology has been in use since before we had computers; it was commonly used even when we utilized mainframes that used magnetic core memory. There are many ways to use and implement encryption. This article presents the basics of the latest technology.
The RSA public key encryption system derives its initials from the surnames of Ron Rivest, Adi Shamir, and Leonard Adleman, who described the system back in 1977. It is based on the mathematical problem of factoring numbers based on two large prime numbers.
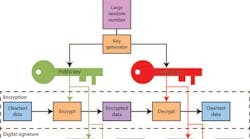
Public key encryption (Fig. 1) is asymmetrical using a generated public and private key pair. The public key is used to encrypt data that can be decrypted using the private key. This allows the public key to be freely distributed, but the private key must remain secure.
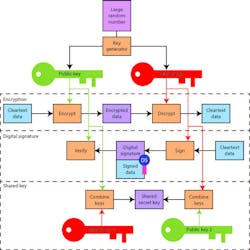
A digital signature uses encryption to sign some cleartext that can be decrypted and verified. The signature is based on the cleartext that often provides additional information that can now be verified to be authentic. Anyone with a copy of the public key can authenticate the digital signature.
One use for digital signatures is to implement digital certificates used in public key infrastructures (PKI). Another use for this asymmetrical key system is to create a shared secret key using two sets of private/public key pairs. The trick is that each side only needs access to its private key and the public key of the other side. These public keys can even be exchanged as part of a protocol like the Diffie-Hellman algorithm. It is more involved than just swapping the public keys, but it can make sure that both sides are the only ones able to generate the shared key.
Asymmetrical systems are useful but with a high computational overhead compared to symmetrical systems that employ a single key. Usually, the two systems are combined with the asymmetrical keys being used to generate or authenticate a shared secret key used for symmetrical encryption and decryption that is usually faster.
A public key system can be utilized with sets of users that cooperate in sharing public keys. This is often referred to a self-signed key approach where a user is their own certificate authority (CA).
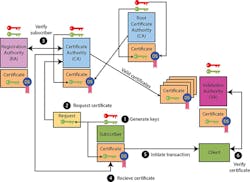
A PKI (Fig. 2) is a system, like the one used with the internet, provides a more secure system that many people can employ to make sure that private/public key pairs are owned by the appropriate entity.
PKI systems include certificate authorities (CAs), registration authorities (RAs) and validation authorities (VAs). A CA can sign a certificate based on its own private key. A CA hierarchy is built by having a CA higher in the hierarchy sign a CA's certificate. The certificate includes not only the public key of the CA, but the ancestor CAs starting at the root CA.
An application like a web browser can utilize one or more root CAs. This allows it to authenticate certificates that have been created using any of the CAs within these CA trees. Most operating systems like Windows, IOS, and Android are delivered with a collection of root CAs. Additional CAs can be added to this list.
The process for getting a certificate is pretty simple:
- First, a subscriber generates a private/public key pair.
- It then sends a request to a CA that includes the public key.
- The CA verifies the subscriber using an RA. Verification may take number of forms. For example, a credit card may be used to verify a subscriber, but other means can be used, as well.
- After verification, the CA signs a certificate and sends it back to the subscriber.
- The subscriber can then use its certificate in transactions.
- Client applications can verify a certificate by first looking at the certificate's expiration date, then looking at the CA that signed the certificate, and finally checking with a VA to make sure the certificate has not been revoked.
Some small system implementations have a CA, RA, and VA on the same server but typically they are distributed among different servers. A CA can have multiple RA and VA servers associated with them. A CA hierarchy is typically used because the root CA must be kept secure or everything falls apart.
Certificates typically include an expiration date. Certificates can be renewed with the same public key. A single year is a typical duration for a certificate. The reason is that a VA is needed to maintain valid and revoked certificate lists. The latter is used to determine certificates that have been revoked prior to their expiration date. Many applications do not assume that a certificate can be revoked. Likewise, most root CA certificates have very long durations.
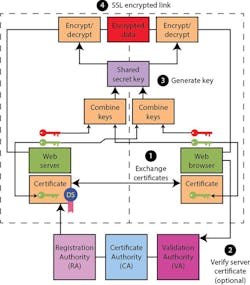
Secure or authenticated communication—e.g., web browser/server connections—often employs secure socket layer (SSL) protocols (Fig. 3). SSL can utilize a range of encryption technologies and protocols, including PKI-based support.
SSL support can be implemented using self-signed certificates, but typically servers use a certificate obtained from a PKI system. This is especially true for sites where monetary exchanges are involved.
In general, the SSL protocol starts by having participants exchange certificates so they each have the other's public key. If a PKI system is used, the participants can also be verified; otherwise, only an encrypted link can be guaranteed. This is one-sided, with a web browser authenticating a web server—not the other way around—although an IoT device and an IoT server may want to authenticate in both directions.
The actual SSL encryption is normally done using a more-efficient symmetrical key system. The asymmetrical public keys are used to initiate the process.
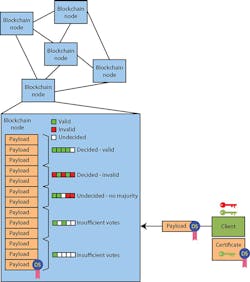
Encryption can be used for a range of chores. One relatively new one involves blockchain technology (Fig. 4). Blockchain systems implement a cooperative, distributed, write-once database. Blockchains can be implemented in many ways and are used for many applications, including cryptocurrencies like Bitcoin.
Of course, blockchain communication and identification are based on the encryption systems we have already examined. The nodes within a blockchain system operate in a cooperative fashion, maintaining a database of transactions that are managed in a very controlled but asynchronous fashion.
Essentially, a client can send a transaction to a node. The transaction is distributed among the other nodes that compare the information in their version of the database. A transaction is validated within a database when enough of the nodes agree that the transaction is valid.
At any point in time, a node's database may contain a collection of transactions that have insufficient votes associated with them. Typically the nodes will have slightly different database states, but the growing collection will be consistent within the group. Unlike a conventional relational database, the blockchain system does not have atomic operations.
The way the blockchain database is built is important. First, transactions must be digitally signed and the collection is also built upon each transaction. How this is done varies based on the data being maintained and how transactions are validated. A cryptocurrency will base its operation on the exchange and distribution of the currency.
The use of encryption allows many applications to operate securely, but this necessitates a number of assumptions and requirements. Many systems require systems like PKI to operate securely with proper protection of secrets. Major issues can arise if this is not the case.