Managing Hardware Root of Trust for Multiple Serial Devices
What you’ll learn
- How to secure the boot process.
- How Lattice Sentry protects serial memory-based solutions.
- Where Mach-NX fits into the solution.
A hardware root of trust (HRoT) is the basis for most secure computer systems. This typically includes secure key storage and hardware to use these keys to verify the contents of memory before host processors can run a program. Some systems incorporate the HRoT into the processor chip, but many rely on off-chip systems to provide such security.
Lattice Semiconductor’s Mach-NX secure FPGA platform is an off-chip solution that’s able to manage one or more serial memory devices. It allows a single system to handle complex, multichip systems in an integrated fashion. The Lattice Sentry system, initially available on the MaxhX03D FPGA, now works with the Mach-NX chips.
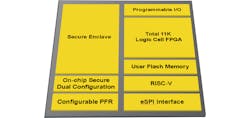
The Mach-NX is an FPGA with a number of hard blocks, including a secure enclave (Fig. 1). It has a configurable platform firmware resiliency (PFR) that supports elliptic curve cryptography (ECC) to detect unauthorized changes in serial memory managed by the chip. The PFR is NIST 800-193 compliant.
The chip utilizes a hard RISC-V core with its own dual flash memory. The dual memory allows it to handle its own over-the-air (OTA) updates.
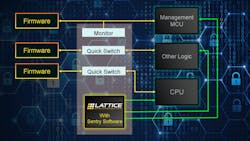
A cryptographically secure immutable ID also is included. By handling its own secure boot, the chip is able to manage the booting of external devices that utilize serial memories (Fig. 2). The Mach-NX can just monitor the memory path or sit between the serial memory and its matching host. In the latter case, it checks the memory before the host can even use it. Likewise, this allows the chip to handle OTA updates independent of the host.
The Mach-NX will start the boot process using its own internal memory. It can then check the contents of each serial memory before allowing the matching host to boot. Updates also could be performed at this point. This approach allows the host to utilize the memory as needed, even making changes while the Mach-NX makes sure any changes that would affect the boot process are flagged. Subsequently, the application running on the RISC-V core can determine what should be done. This might involve loading a known-good copy of the contents for the serial memory or preventing the host from booting.
Serial memory interfaces are managed by the Mach-NX’s FPGA. Thus, a single chip can handle different configurations and interfaces. The Lattice Propel Design Environment facilitates creation of an FPGA configuration.
The Mach-NX is designed to prevent various attacks on its content and operation. Because it’s able to operate on its own and maintain secure operations, the chip can be used within Lattice SupplyGuard, which is a secure supply-chain management system also announced earlier. The keys contained in the Mach-NX allow it to manage ownership and features as a product is moved from production to sales and to a customer. This helps prevent unauthorized grey-market production.