Security seems to be at the top of everyone’s list of important design criteria, but implementing it can prove to be difficult. Arm’s Platform Security Architecture (PSA) is designed to change that for Cortex-M microcontrollers. The architecture-agnostic PSA is designed to be used in applications where a full Trusted Execution Environment (TEE) is too large or complex. As of now, Cortex-A platforms support Arm’s TrustZone and TEEs. Efforts like the Trusted Computing Group’s DICE also address this low-end space.
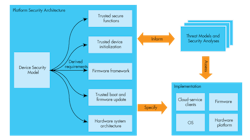
The PSA consists of three parts (Fig. 1). These include Threat Models and Security Analyses, architecture specifications for firmware and hardware, and an open-source reference implementation.
1. The PSA consists of three parts: the Threat Models and Security Analyses, architecture specifications for firmware and hardware, and an open-source reference implementation.
Arm analyzed a range of IoT use cases and crafted a set of English-language Protection Profiles designed for developers who aren’t security specialists. The profiles establish a set of Security Functional Requirements (SFR) for the Target of Evaluation (TOE).
A typical analysis and profile for a smart metering system would include assets like protection of the meter from threats such as remote software attacks, a set of objectives such as providing strong crypto support, and hardware requirements like hardware-based key storage.
The PSA documents would define the Device Security Model, the Trusted Device Initialization, the Trusted Base System Architecture (TBSA-M), Trusted Boot and Firmware Update support, the PSA Firmware-M Framework, the secure processing environment, and the PSA Trusted Functions. Arm has a PSA whitepaper that provides more details. Through TBSA-M targets new ARMv8-M platforms, vendors can also integrate support on ARMv7 platforms.
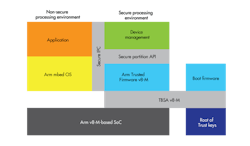
2. A typical PSA implementation includes separate computing environments as well as root support for secure booting and key storage.
An example implementation would include features such as secure boot and secure key storage, trusted firmware, and system partitioning (Fig. 2). The Trusted Firmware-M is an open-source reference PSA implementation for the ARMv8-M architecture.
Arm is providing PSA support of its mbed OS, an open-source operating system for Cortex-M platforms. In addition, the Arm Keil development system provides secure and non-secure software development, debug, and verification.