Reap More Data Security from Memory with an Integrated Secure Element
Car security no longer relates to function alone. Whether an infotainment system, onboard electronics, or system architecture for autonomous driving, a modern car is a rolling IT network. That’s why vehicle manufacturers increasingly need to take data and communication security into account. Specialist memory and security solutions offer new approaches.
In 2015, AUDI AG, BMW Group, and Daimler AG paid a total of 2.8 billion euros ($3.02 billion) to take over Nokia’s geodata business. The significance of navigation systems at the advent of autonomous driving could not be clearer. Exact positioning is required for highly automated driver-assist functions and for fully autonomous driving.
For such positioning, the most important components are the expected accuracy of the GNSS Galileo system, when it’s finally complete, and accuracy of high-quality maps. Maps from Here Technologies (previously Nokia, previously NAVTEQ) are, according to the company, already used in four out of five car navigation systems in Europe and North America. The investment in 2015, and all of the additional progress made since then, seems to have been worthwhile.
But how are navigation systems actually protected from software pirates? Do licensees deploy all of the available technical functions sufficiently to protect data? The answer is most probably no.
Usually, SD Memory Cards are employed to load map data into a navigation system. Generally, the data image on those is encrypted—but only using software. This type of copy protection is known to be relatively easy to bypass, because the content encryption key must be derived somehow from the publicly readable card identifier resident on the very same card.
An attacker—not knowing the encryption key—simply clones a card entirely; for instance, by copying the encrypted content and cloning the card identifier. This is the reality on the internet! There’s no license or counterfeit protection built in, nor the option of a reliable central license inventory to prevent the cloned card from being used.
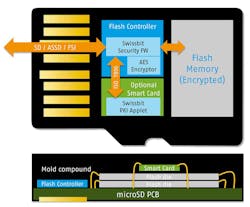
Copy Protection, on the other hand, requires a hidden authentication feature that can’t be pirated. There are already solutions that use flash-memory cards in the field. For example, the manufacturer Swissbit specializes in durable memory products for industrial use with long-term availability. It offers memory cards with security features that combine a flash-memory chip, an optional SmartCard, and a flash controller (Fig. 1).
Special firmware, for instance with integrated AES and HASH algorithms, allows for a multitude of secure application scenarios. The optionally integrated JavaCard SmartCard is certified to Common Criteria Level EAL 5+. The combination of the identifier with a standard data memory offers a technically elegant solution. Tap-proof mobile phones, bodycams or counterfeit-proof cash registers are already secured with this type of card. The simplicity of distribution and content uploading is unaffected.
A high-resolution map update would definitely be a stress test for mobile data plans, both in performance and cost. Home uploading or simple drop-in replacement by a mechanic at the car dealership mandates the level of simplicity required.
An Approach with Potential
Using flash-memory modules with Secure Element offers direct benefits such as gaining control of navigation system data and being able to ensure compliance with license terms. In addition, this approach offers a broad range of application scenarios relating to data protection and cybersecurity in cars.
Infotainment systems are platforms that offer a base for further communications services. These systems are becoming increasingly important as an interface to ICT (information and communication technology) devices and the internet (Fig. 2). When offering chargeable services, receiving valuable media content, paying toll charges, or supporting eCharging use, the matter of a unique identity and, therefore, a secure authentication entity arises again.
Memory cards with an integrated SmartCard offer the ideal solution, particularly because they can be securely paired with the vehicle and replaced so easily should it be necessary. Car subassembly manufacturers should pay careful consideration before abandoning an SD Card reader as an interface on infotainment devices. When using the right cards (Fig. 3), new functions can be retrofitted and continuously secured at the highest cryptographical level.
Security as a Safety Aspect
In recent years, increasing networking within and outside the car—e.g., Car2Car Communication—has made the issue of security in the sense of defending against cyberattacks a subject for debate, mainly against the background of the possible impact on functional security. However, the option of using memory modules with Secure Element also offers solutions in the context of data traffic in vehicle electrical systems.
The communication of electronic control units (ECUs) via bus systems could be encrypted if, for example, an eMMC with Secure Element serves as a Trusted Platform Module at the nodes (Fig. 4). Thanks to this authentication feature, the risk of tampering with in-vehicle communications can be eliminated.
The car has two main categories of functional safety: security-related and non-security-related. This distinction is generally made so that, for instance, the infotainment system has no access to safety-related systems on the platform. Yet, even for non-safety related elements, the ability to provide flexible and sustainable cybersecurity is required because the lifecycle of a car can easily exceed 10 years. By then, many as yet unidentified and emerging requirements will need to be fulfilled, such as toll collection, billing of e-charges, chargeable value-added media services, subscriptions for updates to navigation map data, and much more.
The added value of the infotainment system will increase as it serves to perform increasingly more important tasks. On the other hand, automotive IT systems will inevitably be exposed to ever more sophisticated attacks over time.
For security reasons, and as a precaution, a flexible replaceable Secure Element in a memory card should be provided for the protection of future business. Germany’s Federal Office for Information Security (BSI) requires the consistent application of state-of-the-art technology, which can’t be achieved for security solutions that are several years old, and especially those purely based on software security—that offers the required flexibility but never the required long-term security. Therefore, maintaining the option of a replaceable hardware security module is advisable.
In addition to easy modification and retrofitting, different software-dependent configurations of the same model are easy to manage. All variants are configured and, with the help of the Secure Element on the memory card, those purchased by a customer are activated. It’s an effective way to simplify the variant diversity in production.
Also, when deciding between using a soldered-in or a removable flash memory, the adverse effects on the durability of the NAND chips in the memory modules, caused by a combination of frequent access and challenging thermal and environmental conditions encountered in a car, should be considered. In short, with memory boards that can’t be easily replaced by a mechanic, significantly more expensive solutions need to be accepted.
Conclusion
Protecting maps using memory cards with a security feature is just one example of an application where the combination of memory card and SmartCard allows for a higher degree of control and security. With applications across information and communication technology and consumer electronics, further security considerations, development cycles, and market mechanisms appear beyond those encountered in automobile manufacturing.
Here, the use of a replaceable standard element provides the ability to create a high level of security using hardware-based cryptography. Meanwhile, it remains permanently flexible to accommodate the integration of additional services.
Hubertus Grobbel is Head of the Security Products Division at Swissbit AG.
About the Author
Hubertus Grobbel
Head of the Security Products Division, Swissbit AG
Since July 2019, Hubertus Grobbel has been Vice President Security Solutions at Swissbit. Previously, he oversaw the securities solutions division as Head of the Security Business Unit. He has more than 15 years’ experience in the development of highly innovative security products and in the development of new applications and markets for security solutions to Swissbit. Hubertus holds a degree in electrical engineering from the Rheinisch-Westfälische Technische Hochschule Aachen (RWTH Aachen University).