It’s funny how when you think you know what a company does, it goes and talks to a customer and comes away with something even more interesting. Such is the case with UltraSoC, which just came out with what it calls “Bare Metal Security” to address the all-consuming issue of security for the Internet of Things (IoT).
I bumped into UltraSoC’s CEO, Rupert Baines (ex-picoChip), at his booth at an event earlier this year, but we didn’t really get to talk about his new venture, except to say it had to do with inserting the hooks to accelerate IC test, verification, and debug. Then I noticed the recent Bare Metal Security announcement and so we connected.
UltraSoC’s initial goal was to simplify the test and debug of really complicated system-on-chip (SoC) IC designs with dozens of cores, hundreds of IP blocks, and millions of transistors, all involving complex hardware and software interactions and dependencies that have become enormously difficult to debug.
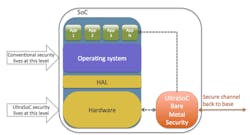
Bare Metal Security bypasses the system software and is not detectable by hackers, yet can monitor any attempts to accessing protected memory and other unusual activity, then message that out to a laptop or server in a data center.
“JTAG is 30 years old, ARM has CoreSight, which is old enough to go to college, but those were developed before heterogeneous [multicore] SoCs with cores from multiple different vendors,” says Baines.
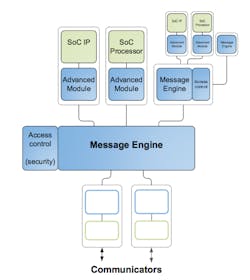
So UltraSoC set about developing silicon IP that a developer can drop into a design and which can monitor all the different elements (cores, buses, custom logic), and non-intrusively provide rich, high-level information on what’s going on, all at wire speed without affecting the target system and without introducing latencies.
“We can efficiently laser in and find a problem, even if that problem is intermittent or sparse, and when it does happen—bam! —we’ll find it and report it out for the developer to fix,” Baines says enthusiastically.
This shortens the product development cycle, and when the product does get into the field, there are fewer bugs and less chance of recalls or liabilities.
The amount of IP required to do the monitoring, and its percentage of overall final die size, varies between 1% at a basic level, up to 7% with maximum monitoring, such as for safety critical automotive applications, where UltraSoC has already found a home. As the die overhead is constant, the percentage goes down as the chip gets bigger.
While the main application has been debugging during development, where Baines notes that it can shave up to two months off the design schedule for a complicated chip, a funny thing happened when talking with one customer.
“They asked if we could detect deliberate bugs, like if someone did something on purpose to make the system go wrong,” says Baines. “We said ‘sure’ and developed extra layers of silicon IP and various software analytics to make that easier. Same functionality, but for a different application.”
Little did they realize at the time, but they were starting to address what is now a burgeoning need for hardware security in IoT devices. Software-based solutions just don’t cut it anymore.
UltraSoC’s IP is orthogonal to the IC functions, so while it can monitor, it cannot affect those functions. Also, by virtue of being orthogonal, it cannot be detected by an intruder and disabled. As a result, the Bare Metal Security feature can monitor the system functions and ensure malware is not affecting behavior and there are no unpermitted accesses. If there are, a message can be sent via secure channels.
All told, this orthogonality, its visibility into the entire SoC, and the lack of processing overhead (unlike typical security software) makes Bare Metal Security seemingly ideal for hardware security applications, especially in battery-driven devices. Not as a full solution, but certainly as an adjunct to or in concert with other security and reliability features. It’s hard to have “too much” security, especially if the overhead and cost of adding it is marginal.