Download this article in PDF format.
On the surface, this sounds ridiculous: A lobby fish tank gets attacked by hackers. Why would anyone want to break into a fish tank (Fig. 1)? But in this case, the aftermath was serious. The fish tank was inside a casino and its temperature and lighting were controlled by an internet-connected system. The break-in provided the hackers with an entryway into the casino’s network—and its sensitive database containing information about high-roller clients.
1. What are the odds that this lobby aquarium could get hacked? It’s fair game if it has an IoT component and is unsecured.
In our digital age, marked by a burgeoning number of Internet of Things (IoT) devices, it’s imperative for designers to design with security in mind. High-value products—often prized for their underlying data—are targets for counterfeiting and cloning, unauthorized use, and malware, just to name a few attack types. Medical tool developers, for example, have had their products harvested from medical waste and later placed back into the supply chain. Fake sensors have been found in industrial control and automation systems. The list goes on.
Cybercriminals have become increasingly sophisticated in attacking the ICs that implement security in an embedded system, using techniques and sophisticated equipment such as reverse-engineering, microprobing, and focused ion beam (FIB). For these reasons, security implemented in software on a general-purpose microcontroller doesn’t go far enough in protecting the design.
Embedded security ICs, on the other hand, provide more robust protection, and they continue to offer advanced security features to stay ahead of the attackers. The latest secure hash algorithm, SHA-3, is one such feature that’s now available in hardware. This article covers what you need to know about protecting your embedded design with SHA-3.
Strong, Efficient, and Cost-Effective Security
Hash algorithms turn a digital message into a short message digest for applications such as digital signatures. Any change in the original message causes a change in the digest, which makes it easier to spot intentional or unintentional changes to the original message.
Secure hash algorithms produce digests that are irreversible and unique. Because of their irreversible nature, if you only had the hash digest, you wouldn’t be able to determine the original input data. Their uniqueness means that two different pieces of input data won’t produce the same hash. However, if you do encounter the same hash from two different values, then you’ve got a collision—a broken hash function that signals a vulnerability.
SHA-3, developed by a renowned European cryptographic team, is based on the KECCAK cryptographic function. The KECCAK function consists of a structure that uses sponge construction,1 which represents a class of algorithms that take an input bit stream of any length to produce an output bit stream of any desired length. It’s considered to be strong because of its intricate, multi-round permutation f, which is the function that transforms the state memory of the hash algorithm. The KECCAK function has the flexibility to support symmetric cryptographic functions, including hashing, pseudo-random number generation, and authenticated encryption.
Released as the latest secure hash algorithm in 2015, SHA-3 is the first cryptographic hash algorithm that the National Institute of Standards and Technology (NIST) has adopted through a public competition and vetting process. It’s efficient to implement in silicon as well as in software via Boolean operations and, compared to other security algorithms, is also cost-effective. SHA-3 is ideal for securing embedded subsystems, sensors, consumer electronic devices, and other systems that use symmetric key-based message authentication codes (MACs). The algorithm is also faster than its predecessors, with a reported average speed of 12.5 cycles per byte on an Intel Core 2 processor.2
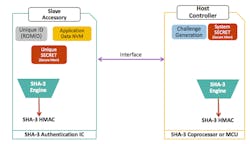
SHA-3 provides a secure one-way function. This means you can’t reconstruct input data from the hash output, nor can you change input data without changing the hash. You also won’t find any other data with the same hash or any two sets of data with the same hash. As an example of how SHA-3 works, let’s consider an end application that, at a system level, features a peripheral or slave accessory that integrates a SHA-3 authentication IC and a host controller with a SHA-3 coprocessor or microcontroller (Fig. 2).
2. Fundamental elements in a SHA-3 authentication model.
The slave accessory has a unique secret and the host controller has a system secret. In the authentication process, the first step is for the host to securely compute the unique secret that’s stored in the slave IC.
To do this first step, the host requests the ROM ID from the slave and inputs it, along with its own securely stored system secret and some compute data, into its own SHA-3 engine. Next, the engine computes a SHA-3 hash-based MAC (HMAC) that’s equal to the unique secret stored in the authentication IC. Once it securely derives the unique secret in the slave IC, the host controller can perform various bidirectional authentication functions with the authentication IC.
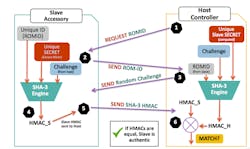
An example is a challenge-and-response authentication sequence to prove that the accessory is genuine (Fig. 3). Here, the host requests and receives a ROM ID from the slave. The host also produces a random challenge and sends it to the slave accessory. The slave accessory then inputs its unique ID, unique secret, and the challenge into its SHA-3 engine to compute a SHA-3 HMAC. This HMAC is returned to the host. During the process of this sequence, the host computes its SHA-3 HMAC with the unique slave secret, the challenge, and the slave’s ROM ID. The slave accessory is verified to be authentic if the HMACs are equal.
3. This figure illustrates the flow to authenticate a slave accessory via a challenge-and-response sequence with SHA-3.
The KECCAK function upon which SHA-3 is based has demonstrated the ability to resist known attacks with a minimum complexity of 2n (n = hash size), and it boasts a wide safety margin.3
SHA-2 vs. SHA-3: What’s the Difference?
While SHA-3 presents the latest secure hash algorithm available, SHA-2 remains viable for some applications. SHA-2 shares a similar mathematical implementation with SHA-1, but, with its longer bit length and use of larger inputs and outputs versus SHA-1, it has demonstrated the ability to provide better protection than its predecessor.4 In fact, the first SHA-1 collision was calculated back in 2017, and this occasion shined a spotlight on its growing vulnerability.
Meanwhile, SHA-2 continues to be implemented in some commonly used security protocols, including Transport Layer Security (TLS) and Secure Sockets Layer (SSL). Bitcoin and other cryptocurrencies rely on SHA-256 to verify transactions and calculate proof of work. Many U.S. government applications utilize SHA-2 to protect sensitive unclassified information. The algorithm is also integrated into many commercial security ICs on the market.
NIST still considers SHA-2, which consists of two similar hash functions (SHA-256 and SHA-512), to be secure and notes that SHA-3 complements it while providing greater diversity.5 SHA-3 has four cryptographic hash functions with these different digest bit lengths: SHA3-224, SHA3-256, SHA3-384, and SHA3-512, plus two extendable output functions (SHAKE-128 and SHAKE-256). In these output functions, the -128 and -256 extensions refer to the function’s security strength. Extendable output functions can be used for full domain hashing, randomized hashing, and stream encryption, as well as to generate MACs.6
Cryptography Expertise Not Needed with Security ICs
Implementing SHA-3 security in an embedded system doesn’t require cryptographic expertise if it’s done via a security IC. This is an important consideration, as it’s not uncommon for embedded designers to have limited cryptography expertise.
There are now secure authenticators available with the SHA-3 algorithm integrated. Secure authenticators provide symmetric and asymmetric algorithms, bidirectional authentication, and secure system data storage, use counting, memory settings, and general-purpose I/O (GPIO), so they’re suitable for a number of applications.
To determine whether it would make sense to integrate hardware-based security into your design, ask yourself these questions:
- Is there an existing problem that could be solved with security?
- Could my system be a target for counterfeiting or improper use?
- From a safety and quality perspective, is it important for my sensors, tools, and modules to be genuine?
The newest secure authenticators on the market bring together the SHA-3 algorithm with physically unclonable function (PUF) technology. PUF technology protects against invasive and non-invasive attacks by utilizing the random electrical characteristics within silicon to produce a per-IC unique key. The key is generated only when needed and erased when no longer required.
An attempt to probe or expose silicon designed with PUF causes the sensitive electrical characteristics to change, rendering the PUF circuit to be useless. SHA-3 and PUF together elevate the level of protection available to embedded designs, preventing counterfeiting, aftermarket cloning, unauthorized usage, and invasive attacks.7
Conclusion
While public attacks on SHA-2 have been happening for more than 10 years now, has yet to be a successful breakthrough. But as with SHA-1, it’s only a matter of time before SHA-2 is deemed untrustworthy, particularly as it uses the same Merkle-Damgard engine as SHA-1.
Migrating from SHA-2 to SHA-3 has been slow, partially because of a lack of software and hardware support. The migration process, however, should be somewhat similar to the move from SHA-1 to SHA-2. And at least for embedded systems, there’s at least one secure authenticator available with SHA-3 support that will make it easier to protect a smart, connected design.
For more on SHA-3 and how it can help prevent counterfeiting of medical disposables, check out this upcoming webinar being co-sponsored by Maxim Integrated and Digi-Key.
Scott Jones is Managing Director of Embedded Security at Maxim Integrated.
References:
1. https://keccak.team/sponge_duplex.html
2. http://www.drdobbs.com/security/keccak-the-new-sha-3-encryption-standard/240154037
3. http://www.drdobbs.com/security/keccak-the-new-sha-3-encryption-standard/240154037
4. https://www.csoonline.com/article/3256088/why-arent-we-using-sha3.html
7. https://pdfserv.maximintegrated.com/en/an/Secure-Your-Embedded-Systems-with-SHA3.pdf