>> Website Resources
.. >> Library: TechXchange
.. .. >> TechXchange: Embedded Software
.. .. .. >> Topic: Ada and SPARK
A web application is a client-server program that uses the web browser to run the client side. Typical web applications include online web mail, online banking, online shopping, and others. The client side is responsible for the interaction with the user and displaying results obtained from the server. On its side, the server is responsible for storing the user’s data, keeping the data consistency, and updating them according to the user’s interactions.
Security is often underestimated in web application development. It’s an important challenge since the web application has to protect a user’s data from being stolen and corrupted by malicious users. Such corruption and theft often occurs within the server due to software and programming errors.
The CWE/SANS Top 251 gives the list of the most dangerous software errors. A permissive language such as Javascript and Python is more vulnerable than a strongly typed language such as Java and Ada. Several CWE are handled by the Ada language2 and will therefore be caught during the development. This makes an Ada-based server implementation safer and less vulnerable.
Ada Web Application (AWA)3 is a framework to build a web application in Ada 2012. The project was started in 2011 with the initial idea to implement several Java technologies in Ada that were proven to be successful in web-application development. Indeed, the Java EE, now Jakarta EE, defines a collection of standard APIs for an enterprise to build a web-application server. The AWA framework was presented at the FOSDEM 2019 Ada devroom and at AdaCore TechDays 2019.
The AWA framework provides several ready to use and extendable modules that are common to many web applications. This includes the login, authentication, users, permissions, managing comments, tags, votes, documents, and images. It provides a complete blog, questions and answers, and a wiki module. Several web applications are already using AWA as a core technology: the Ada France website (https://www.ada-france.org), the Jason project management application, the Atlas demonstrator, and the author’s personal blog (https://blog.vacs.fr).
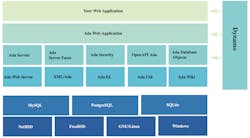
An application server built with AWA is made of several Ada components and libraries that are packaged and interact together. First, it will use the Ada Web Server to serve the HTTP requests (see figure). It will be able to connect to several databases, including PostgreSQL, MySQL, and the embedded SQLite database by using the Ada Database Objects library. The framework handles web requests through Java servlet technologies implemented in Ada by the Ada Server and Ada Server Faces libraries.
Starting a project from scratch is never easy. To solve this, the AWA framework comes with a tool that helps in setting up the project. The tool, Dynamo, is a command-line tool that provides several sub-commands to help in several development tasks. After setting up the project, it’s used to generate Ada database mapping code and simplify several development tasks.
The AWA framework deals with the most important challenges facing a web developer.
Database Access
A first challenge on the server side is the interaction with the database. To help in this task, the AWA framework uses object-relational mapping (ORM). The data tables contained in databases are described using either a UML class diagram or an XML or YAML description file. From these descriptions, the Dynamo tool will generate the database SQL schema as well as the Ada packages that allow the application to access the data table content easily.
The ORM will map each database table in a specific Ada tagged record. The Ada tagged record provides operations to find, insert, update and delete elements from the mapped SQL table. By using such Ada type, the application continues to benefit from Ada’s strong typing, and it doesn’t have to bother with SQL issues. The use of the ORM makes sure that the application isn’t vulnerable to SQL injection.
Access Control
When the server must process a request, it’s necessary to verify at different steps whether the user is allowed to perform the operation. It’s the responsibility of the Ada Security library to perform this task.
First, the library provides an authentication framework that allows to implement the OAuth 2 standard described in RFC 6749.4 Having authenticated a user, the Ada Security library makes it possible to verify whether a user has the permission to access a resource. The application defines the permissions that must be enforced and associate a security policy manager for each of them. The security policy manager is responsible for checking whether the permission is granted or not based on the user’s credentials.
At different places in the application, it becomes possible to check one or the other permission. The Ada Security library will authorize or not authorize the access based on the authenticated user and the security policy associated with the permission.
Web Presentation
Interaction with the client browser requires that the server validate the request parameters it receives, as well as generate the HTML content for the browser. In this case, the AWA framework implements the Java Server Faces standard component-oriented user interface defined by the Java EE platform. Fully implemented in Ada, the Ada Server Faces library benefits from the mechanisms defined in the Java JSR 344 standard.5 The Java XML Facelet templates are used to describe the content of views to be rendered. Such templates also describe how to handle the input parameters sent by the browser. They are verified and checked by the Ada Server Faces library.
The link between the XML Facelet template and the Ada runtime is made through another Java standard: the Java Expression Language described by JSR 245.6 The Ada EL library implements the standard and creates the link between the XML presentation page and the Ada application variables.
The use of Ada to handle request parameters and generate the HTML content reduces the vulnerabilities of the final application. At every stage, we benefit from the Ada strong typing mechanisms.
REST API
The single-page web application traditionally uses a Javascript framework that runs within the client browser. Frameworks like ReactJS, AngularJS, and Vue.js interact with the server by using REST API. Such an API has become so common that the OpenAPI initiative was created in 2015 by several companies, including SmartBear, Google, Microsoft, IBM, and PayPal.7 From this initiative emerged the OpenAPI specification,8 which makes it possible to describe any REST API provided by a server.
By writing a description of the server REST APIs, it becomes possible to generate both the client and server bindings. Indeed, the OpenAPI Generator9 supports more than 33 different programming languages for the client binding and 15 for the server binding. Of course, Ada is supported for both client and server binding. By using a generated Ada server binding, the task to write the REST API is simplified.
When a client makes a REST request, it’s first received by the Ada Web Server library that handles the HTTP protocol. It will then give the request to the Ada Servlet library, which will process the request through the OpenAPI-generated binding.
Through this process, the Ada Security library is involved to verify the permissions associated with the REST operation. Finally, when the operation is allowed and the request parameters are validated, the OpenAPI binding will call the Ada operation to handle the request. Upon successful completion of that operation, the OpenAPI binding will format, either in XML or JSON, the response that’s returned to the client. At each of these levels, Ada strong typing reduces several vulnerabilities, including buffer overflows, making the REST API implementation safer.
Conclusion
From the database connection to the client browser interaction, it’s possible to benefit from the strength of the Ada programming language for web development. At each level, the use of Ada eliminates several software and programming errors by having the compiler verify several of these errors. Ada isn’t reserved to software-critical embedded environments, and using a framework such as AWA makes sure that the security constraints are enforced in the final web application.
Stéphane Carrez is Senior Software Engineer at Twinlife.
References
1. CVE/SANS Top 25 Most Dangerous Software Errors, https://cwe.mitre.org/top25
2. AdaCore Technologies for Cyber Security, Roderick Chapman and Yannick Moy
3. Ada Web Application, https://github.com/stcarrez/ada-awa
4. RFC 6749, The OAuth 2.0 Authorization Framework
5. JSR 344, Java Server Faces
6. JSR 245, Java Server Pages, Chapter 2 Expression Language
7. OpenAPI Initiative, https://www.openapis.org/
8. OpenAPI Specification, http://spec.openapis.org/oas/v3.0.2
9. OpenAPI Generator https://github.com/openapitools/openapi-generator
>> Website Resources
.. >> Library: TechXchange
.. .. >> TechXchange: Embedded Software
.. .. .. >> Topic: Ada and SPARK