WPA2 is the security protocol for Wi-Fi. It replaced WEP, which was hacked many years ago. While WEP is still supported by most wireless access points, WPA2 is now the recommended security measure. Unfortunately, WPA2 has its own security issues.
The United States Computer Emergency Readiness Team (US-CERT) is a part of the U.S. Department of Homeland Security (DHS). The CERT Coordination Center (CERT/CC) has issued CERT/CC “Vulnerability Note VU#228519, Wi-Fi Protected Access II (WPA2) handshake traffic can be manipulated to induce nonce and session key reuse.” According to the note:
“Wi-Fi Protected Access II (WPA2) handshake traffic can be manipulated to induce nonce and session key reuse, resulting in key reinstallation by a wireless access point (AP) or client. An attacker within range of an affected AP and client may leverage these vulnerabilities to conduct attacks that are dependent on the data confidentiality protocols being used. Attacks may include arbitrary packet decryption and injection, TCP connection hijacking, HTTP content injection, or the replay of unicast and group-addressed frames.”
This latest attack is now known as a Key Reinstallation AttaCKs, or KRACK. KRACK was revealed by a postdoctoral researcher at the Catholic University of Leuven in Belgium, Mathy Vanhoef. Vanhoef’s KRACK website provides a very good description of the problem. His technical research paper, “Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2,” is also available.
The method of attack does not compromise the encryption process, but it does provide avenues of attack that can lead to various man-in-the-middle attacks that would further compromise communication. The attack is based on how WPA2 is typically implemented and affects most of the Wi-Fi access points, as well as Windows, MacOS, iOS, Linux kernel 2.4 and later, and Android 6.0 Marshmallow.
Android 6.0 and Linux have an additional issue, owing to a common bug that causes the encryption key to be rewritten to all-zeros. Windows and iOS do not fully implement the WPA2 protocol and do not have this issue.
How it Works
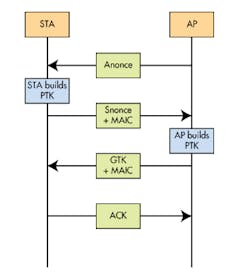
WPA2 uses a four-way handshake mechanism between the wireless access point, known as the authenticator, and a device, known as the supplicant (see figure). It allows the access point (AP) to determine that the device/station (STA) is allowed to use the wireless network. Essentially it is checking that the device’s password, also called a pre-shared key (PSK), is valid. It does so without transmitting the password directly. The two stations then use a generated shared secret key called the Pairwise Master Key (PMK) for ongoing encrypted communication.
The handshake starts with the AP sending a nonce (Anonce), a unique random number, to the STA. Nonce means “number used once.” The STA responds with its own nonce (Snonce), along with Message Authentication and Integrity Code (MAIC), sometimes referred to as just Message Integrity Code (MIC). Both sides can now create a Pairwise Transient Key (PTK) by concatenating the PMK, Anonce, SNonce, AP MAC address, and STA MAC address. The AP also sends the Group Temporal Key to the STA. The STA responds with an acknowledgement (ACK) to complete the handshake. The STA and AP can now exchange data securely using encryption.
The hack essentially captures the third packet with the GTK+MAIC and resends it, causing the STA to reset the handshake process. The protocol allows this because the packet could be lost or corrupted. Likewise, the ACK could be lost. The handshake can be repeated up to three times. The hack then allows the attacker to decrypt traffic from the STA to the AP. The attacker can also introduce packets into the data stream.
Security in Depth
KRACK is a problem, but it brings up the issue of security in depth, and why it is always important not to rely heavily on a single aspect of security. For example, using a WPA2 connection to browse a site that uses HTTP and passwords makes you potentially vulnerable to a KRACK attack, but using a VPN or HTTPS over a hacked wireless network is simpler than using an open Wi-Fi network with respect to potential attacks. The use of VPNs or HTTPS connections adds yet another layer of security that must be breached by an attacker to gain access to secured information.
Security in depth is a design approach that needs to be utilized when developing applications from the start, as opposed to adding protection after the fact, or relying on a single secure communication methodology like WPA2 (which can be costly and possibly ineffective).
This means that employing different forms of security at key points can help mitigate problems that may arise. For example, over-the-air (OTA) updates for self-driving cars have been in the news recently. Securing the update process includes using an encrypted pipe for delivery of the update, but there are typically many other steps that involve security and authentication. These include the use of secure boot so that only signed copies of code will be executed, using authentication to make sure the request to do the update is valid, and so on. That doesn’t mean it will be impossible to compromise a system, but it will be much harder—e.g., an attacker would have to overcome many hurdles to make changes to a self-driving car.
What to Do About KRACK
The problem with KRACK is that the vulnerability is part of the WPA2 standard. On the plus side, the problem is actually easy to fix by changing the software to eliminate the resending of one-time keys. This will likely be part of soon-to-be-released updates for current software. The downside is that not all software can or will be updated.
Older systems are unlikely to receive any changes, although many older systems do not actually have the problem. Also, changing one side of the communication link can fix the issue, at least for that pair of devices, so an updated smartphone accessing an access point without changes can still eliminate the vulnerability.
In the meantime, assume a WPA2 network is an open Wi-Fi system, and use HTTPS for browsing and a VPN for other communication. There are some caveats, as some websites have improperly configured HTTPS support.
Bottom line: Not all WPA2 implementations are created equal, and some can be compromised in some fashion. Still, it is possible to fill the hole with updated software on at least one side of the communication link.