Arm’s Cortex-A family handles heavy-duty operating systems like Linux, while the Cortex-M microcontroller typically runs an RTOS. Designing a system for a Cortex-M tends to be relatively easy compared to its higher-performance sibling because the micros have all of the memory on-board and are often single-chip solutions. Even single-core Cortex-A systems are harder to build around, and multicore solutions usually have high-speed interfaces to go along with them.
One way to simplify Cortex-A utilization is to use a system-in-package (SIP) like Octavo Systems’ OSD335X-SM. It integrates a TI AM335x based on a Cortex-A8 plus DDR3 memory and a EEPROM. The device also has a PMIC.
Another approach is to use a system-on-module (SOM). SOMs are small printed-circuit boards (PCBs) that can be mounted on another PCB or plugged into a socket, depending on the implementation. This also hides the complexity of the system, and the carrier board associated with the SOM is usually easier to lay out in addition to being less costly to build. For example, a carrier board might be a single- or dual-layer PCB, while the SOM will be a multilayer board.
Microchip’s SAMA5D27 (Fig. 1) is a SOM with a SIP on it. The module provides a 500-MHz Cortex-A5 and up to 128 kB of DDR2 memory. A designer needs to add power support and an 8-MB QSPI serial program memory. The chips support eXecute-in-Place (XIP) operation from the latter. An Ethernet PHY allows the on-chip Ethernet interface to connect to an off-board network.
1. The SAMA5D25 SOM builds on a SIP that has the Cortex-A5 and 128 MB of DRAM. The SOM adds an Ethernet PHY, 8 MB of QSPI flash memory, an EEPROM, and a PMIC.
When compared to many other multicore Cortex-A systems, 128 kB of DRAM and 8 MB of flash aren’t a lot, but it’s more than sufficient to run Linux and other operating systems.
The SOM adds a MIC2800-G4JYML Power Management IC (PMIC) chip that provides three power rails for the CPU, VDD I/O, and the SDRAM. There’s a KSZ8081RNAIA 10Base-T/100Base-TX Ethernet PHY plus a 2-kb serial EEPROM that typically holds the Ethernet MAC address.
I got to work with the SAMA5D27 SOM using the SAMA5D27 SOM1 EK1 board (Fig. 2). The board includes the SAMA5D27 SOM and adds features like an ATECC508 CryptoAuthentication security module, a PMOD connector, and a pair of mikroBUS sockets. The latter supports over 300 MikroElektronika click boards. An RJ-45 Ethernet connector, CAN interface, USB connectors, plus a USB-based JLINK-OB debug interface are included. There’s also a supercap for low-power, sleep-mode operation.
2. The SAMA5D25 SOM1 EK1 board includes the SOM, memory, a 10/100 Ethernet port and a security module. It has a PMOD connector and a pair of mikroBUS sockets.
The SAMA5D2 block diagram highlights the family’s other SIP features, including ARM TrustZone support (Fig. 3). The processor chip also has hardware security support, such as secure boot and anti-tamper support, but more on that later. And there’s a 12-channel, 12-bit ADC.
3. The SAMA5D25 is based around a 500-MHz ARM Cortex-A5 with TrustZone support with secure memory and peripheral management.
Communication support includes serial, SDIO, SPI and I2C interfaces plus a pair of CAN-FD interfaces, USB and Ethernet support. A camera interface and a resistive touchscreen controller are in the mix. In addition, a microSD card slot can be used for program storage and typically where Linux and its applications would reside. Storage or wireless support is provided by the full side SD card slot. The USB support can also be utilized for wireless interfaces.
Furthermore, the development board supports the Precision Design Associates (PDA) TM7000B 7-in. PCAP Touch Module. This family of touch displays works with other Microchip development boards.
Loading Linux
Using Linux with the board is almost a no-brainer. Microchip’s AT91SAM community site has everything one needs to get started with Microchip’s SAMx processors, plus forums to handle questions.
The main page for the SAMA5D27 SOM1 has three images for a microSD card that I was able to try out. The images include one for Yocto-based Linux, Buildroot-based Linux and an implementation of OpenWRT. The latter has a web interface while the other two have the familiar Linux command line.
The projects include pre-built images that I downloaded and installed on a microSD card. It was then a matter of booting the system and connecting via the USB serial terminal interface. I normally set up the Ethernet connection and then continue using SSH via Ethernet.
There were pre-built images for the PDA displays, but I didn’t have one of those to test. The only difference would be having a display plus the ability to interact using a USB keyboard.
The advantage of these three examples is the ability to rebuild and extend their base installations. All of the build files are available for download. Of course, this assumes one wants to tinker with the drivers or operating system. The existing images are suitable for application testing. Usually, applications will be cross-compiled much like the operating system.
It only takes an afternoon to get up and running with the system. I didn’t have any Click Boards handy, but getting those working should be relatively easy since they often need only the I2C support that’s provided with the operating system.
Securing the System
Linux has its own security built-in, but features like secure boot come before the operating system is up and running. Cortex-A processors include Arm’s TrustZone support. The Microchip chips also feature hardware security such as anti-tamper support. Unfortunately, those features aren’t utilized by the stock images seen earlier, and the amount of documentation about how to take advantage of the other features is limited.
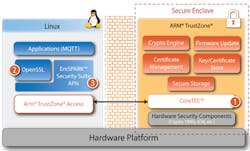
4. Sequitur Labs’ EmSpark provides a security framework for the SAMA5 family that takes advantage of the underlying Arm TrustZone hardware.
The features tend to be utilized in commercial settings, and Microchip works with major customers that often have the technical expertise to take advantage of this hardware. It has also worked with third parties like Sequitur Labs, which created the EmSPARK Security Suite (Fig. 4) to address this hardware. The suite targets Microchip and NXP Cortex-A5 platforms and has some prebuilt images available for testing certain development boards. At this point, I wasn’t able to get one for this particular board. One does exist for the SAMA5D2. Check out Sequitur Labs’ site for more details and changes.
The EmSPARK Security Suite is more than just a way to take advantage of a few features like secure boot. It’s designed to be an end-to-end security environment that’s linked to the cloud and includes deployment and provisioning support. It handles trusted execution environment support, trusted device ID support, and key certificate management.
Developers looking for some open-source support might want to check out the Trusted Firmware-A project on Github.
Summary
Overall, the SAMA5D27 SOM1 EK1 board is a very nice platform. It has all of the needed hardware, including JTAG support for handling hardware development. It exposes most of the interfaces provided by the SOM. And the board has extensive security, but developers will likely need to use third-party support to take advantage of it.