There’s a common never-ending debate in the software development community about what the best programming language is. Java, C, Python, Ruby etc… Developers tend to favor different languages for different tasks, depending on the function they’re looking for, so solving that debate is a highly subjective matter. However, in light of the meteoric rise in open-source vulnerabilities over the past five years, a new question emerges: Is one language safer than the others? Is one more susceptible to hacking?
WhiteSource put out a report that takes an in-depth look into the security of the most popular programming languages. I had a chance to sit down with Rami Sass, Co-Founder and CEO of WhiteSource, to discuss the findings.
Why was the report done?
WhiteSource offers the most comprehensive database of open-source components and their reported vulnerabilities taken from a wide range of sources, including the National Vulnerability Database (NVD), issue trackers, security advisories, and more.
We hoped that we could draw some insights on trends from our research into the seven most popular languages, giving developers some actual data as part of this hot discussion topic over which language is the most vulnerable.
What were the key takeaways?
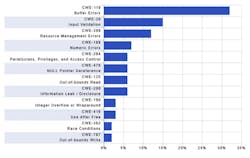
First and foremost was that C was the leading language when it came to reported vulnerabilities. According to our WhiteSource database, vulnerabilities in C comprised nearly half of the reported open-source vulnerabilities, with buffer errors being one of the worst (see figure).
Buffer Errors (CWE-119) have been very common in C for years, but C++ only recently started catching up to its compatriot with an extremely sharp spike in Buffer Error issues reported in 2017.
There are explanations for this, which we delve into in the report itself. But factors concerning the significant outsized role that C plays in development help to put its high number of vulnerabilities into context.
What surprised you?
After a fairly consistent rise in “high” level vulnerabilities over the past few years, including a spike in 2017, there was actually a dip in 2018. There were some other surprises about what has taken over, but you’ll have to read the report to find out.
Based on this report, what should developers consider when it comes to working securely with open-source components?
Every language, like all software really, is going to have its share of vulnerabilities. While languages like C and JavaScript, which are heavily used and receive widespread attention, are going to have high levels of vulnerabilities, we shouldn’t be afraid to keep using them in our products. Instead, we need to think about how we use them securely, managing our usage of them to block open-source components with known vulnerabilities from entering our software from the earliest stages possible.
So long as we are keeping continuous track of which components we’re using in our software, and patching when new vulnerabilities are published, then we should continue to encourage developers to code in whatever language is right for their product.
Rami Sass, CEO and Co-Founder of WhiteSource, is an experienced entrepreneur and executive with vast experience in defining innovative products, leading technology groups and growing companies from seed level to business maturity. Before founding WhiteSource, Rami founded Testology, and before that led development efforts at both CA and at Eurekify (acquired by CA).