Mitigate software obsolescence and cyber risk using application virtualization
The Department of Defense (DoD) spends significant amounts of money addressing software obsolescence and compatibility across the enterprise. Obsolescence is driven by lack of vendor support as hardware systems age and cybersecurity vulnerabilities are exposed. DoD investment in weapons systems is massive and taxpayers demand extended service life; often exceeding 30 years with operations and sustainment accounting for 70% of the total ownership cost.1 Affordable sustainment technologies are needed to maintain operational capabilities without escalating cost. Ultimately, DoD competitiveness with peer and near-peer adversaries is reduced when resources are spent redesigning obsolescent systems. At the fleet readiness centers, the US Navy is tackling this problem by developing sustainment technologies that provide program managers affordable options to manage cyber risk. This article highlights developments in virtual application technology that reduce cyber risk and keep legacy software operational.
Major drivers of software obsolescence are updates to operating systems (OS)—i.e. Windows XP → Windows 7 → Windows 10—and updates to hardware—i.e. 32-bit → 64-bit chipsets. Changing software due to obsolescence drives uncertainty as known-good, fielded software is replaced. Knowing that change is coming as commercial vendors drop support for legacy operating systems and hardware chipsets, how do we sustain our software? The goal is to maintain software capability while mitigating growing cyber risk from new vulnerabilities. Managing cyber risk can be grouped into three categories—low cost, medium cost, and high cost. The low-cost solution is to do nothing and continue to field legacy software on legacy systems. The high-cost solution is to update and patch, rewriting software as needed. The medium cost solution is to create virtual applications that maintain functionality of legacy software as-is and reduce the cyberattack surface of legacy applications. DoD policy drives everyone to the high-cost solution. Updating and patching reduces cyber risk for a limited time, until a new weakness is exposed. An IDC Desktop Maintenance Survey from 2010 puts the client management cost at $270-$340 per year per PC.2 This whack-a-mole approach is prudent for connected systems that are easily updated (ex. business systems). However, it is overly burdensome for systems that are costly or difficult to update (ex. disconnected, stand-alone engineering tools, test equipment, industrial equipment, etc.).
How it works
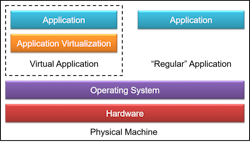
Application virtualization is a process that packages computer programs and their dependencies from the underlying OS into a single executable bundle. The virtualized application is then transportable across operating systems. Virtual applications are not “installed” on the host computer; each application is bundled with the virtualization agent, which launches a virtual environment for the application to run within. That agent provides a translation layer between the host and guest operating systems. See Figure 1. Packaging all necessary dependencies allows for legacy applications to operate on modern operating systems that no longer support legacy software dependencies.
Modern operating systems provide enhanced security, while containing legacy software vulnerabilities in a virtual environment. These additional layers of protection allow operation of legacy software that would otherwise introduce vulnerabilities from software exploits that are no longer patched. Powerful commercial-off-the-shelf (COTS) virtualization tools exist to create virtual applications. Naval Air System Command (NAVAIR) Fleet Readiness Center Southeast (FRCSE) conducted an analysis of alternatives to determine best-of-breed. Multiple software tools including VMware ThinApp, Microsoft Hyper-V, and Oracle VirtualBox were evaluated. Historical product development was also referenced.3 ThinApp provided the best overall agentless virtualization product for Windows-based software.
Building a virtual application can be done in many ways. FRCSE developed the optimal process below:
- Perform a clean install of the application OS into a virtual machine
- Install VMware ThinApp
- Perform a pre-scan capture of the current software state (ex. registry settings, file system, etc.)
- Install and configure application and all dependencies
- Perform a post-scan capture
- Configure virtual application permissions
- Package as a single virtual application executable
The virtual application now runs stand-alone using a just enough operating system (JeOS). The original OS is gone. Only those OS components required to operate are packaged into the virtual application. The guest OS operates within a sandbox. The sandbox is a folder on the host OS that acts as the guest file system. Files cannot be manually added to the sandbox from the host OS. Only the virtual application can access the sandbox. The sandbox can be deleted at any time and the virtual application will reset to initial settings. This allows easy troubleshooting by simply deleting the sandbox to resolve application problems and reset to original condition. Configuration management is improved with virtual applications because software updates are easier to deploy and manage across the enterprise. Currently, most updates are provided to the user with instructions to follow. Human error may result in improper installation, causing configuration variance that is difficult to detect. Installing updates with virtual applications is as simple as deleting one old file and replacing it with the new file. All regression testing is done by the software support activity, ensuring the virtual application will work reliably with less chance for human error. Because the virtual application is not installed on the host machine, it can be run from any location, including directly from a CD.
Using an example of a legacy Windows XP application running on Windows 10; ThinApp packages the application with just enough Windows XP components forVirtual applications
NAVAIR FRCSE has produced and fielded several virtual applications.5 Below is a subset that shows viability on Windows 2000, XP, Vista, 7, and 10 systems. These examples highlight the range of complexity of virtualization. All applications are completely functional and seamless to the user.
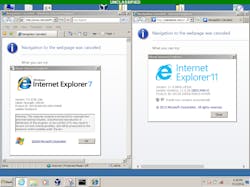
Internet Explorer 7. Native Windows XP 32-bit running on Windows 7 & 10 64-bit host systems. Build time to create the virtual application was about 15 minutes. Executable packaged into a single 66MB file. Figure 3 shows IE7 virtual application running seamlessly side-by-side with native IE11 available on the host system.Application virtualization generally does not work for software drivers because of unique interactions that are not easily virtualized. Some drivers may work depending on the specific situation. NAVAIR FRCSE tested Ext2FS 0.68 drivers to interface the Linux file system in a virtual application with the host OS. Installing the driver on the host OS allowed the virtual application to properly interface with a Linux Ext2 file system. Although application virtualization is typically straightforward, difficulties may arise during the virtualization process. Thorough regression testing is required to ensure proper functionality. Below are examples of issues that arose during the build process of the Teradyne L200 Auto-Converter software.
- Issue: 8dot3 naming convention caused application names to shorten to 8 characters and improperly launch/close. Resolution: Disable 8.3 short naming using the FSUTIL behavior command set to disable8dot3
- Issue: Visual Studio Environmental Variables, INCLUDE, LIB, and Path were not properly mapped. Resolution: Use Visual Studio 2003 SET command during the build process to force the capture of these environmental variables.
- Issue: Program Files (x86) redirects on 64-bit systems and legacy software with C:\Program Files path hard coded won’t look in the (x86) directory. Resolution: Copy %ProgramFilesDir% to %ProgramFilesDir(x64)% during build process.
Going forward
Application virtualization is an advanced technology solution for all DoD programs to reduce cost, improve fielded systems, and mitigate cyber risk. Affordable sustainment technologies must be developed to achieve the Secretary of Defense’s top priority—improving readiness.6-8 Research done at NAVAIR FRCSE shows that virtual applications eliminate unnecessary costs as operating systems change; isolate software from potential hardware obsolescence; reduce fleet hardware footprint by cohabitating multiple software products on a single platform; reduce software conflicts; block user access to restricted executables; provide streamlined configuration management; require no installation; reduce cyberattack surface through isolation of the just-enough operating system; enable continued operation of known good software; and much more. This article presents a technology solution that provides program managers alternative options to significantly reduce cyber risk at a low cost. We present this as an 80% solution that is, “good enough” to maneuver within the cost and performance trade space. EE
Dr. Christopher P. Heagney currently serves as Science Advisor to the Commander of US Naval Forces Southern Command and the US Fourth Fleet. He holds B.S., M.S., and Ph.D. degrees in electrical engineering from the University of Florida. He is a NAVAIR Associate Fellow, authoring nine papers on sustainment technology with two patents pending.
Mr. Lance J. Walker is an Electrical Engineer with NAVAIR. He holds a Masters in computer engineering and a Bachelors in both electrical and computer engineering from North Carolina State University.