Download this article in .PDF format
This file type includes high resolution graphics and schematics when applicable.
It’s clear we live in a world where connections are flourishing between people, “things,” and the Internet. This megatrend continues despite the almost daily news headlines about cyberattacks and ways to boost our online defenses. Long gone are the days when identity or credit-card theft posed the worst of our worries. In today’s hyper-connected world, security concerns will only rise exponentially. Any of the 75 billion devices that Morgan Stanley forecasts will connect to the Internet of Things (IoT) by 2020 will also theoretically be hackable, as is true for anything with an IP address.
Now universally adopted in wide-area networks, Ethernet is poised to play a crucial role as the standard communications backbone in the IoT, too. Its very adaptability, high-performance, low cost, and scalability make Ethernet especially suitable in various Industrial IoT (IIoT) settings, such as smart energy, intelligent transportation, factory automation, and industrial process control—even the connected car.
But if we’ve learned anything from past cyberattacks, it comes down to security. IoT communications, like any other network, will require strong protection against malicious intrusions, including pervasive monitoring, wiretapping, MAC address spoofing, man-in-the-middle attacks, and denial-of-service (DOS) attacks. Of the tens of billions of IoT-connected devices already in use today, few find themselves in physically secure locations. For better or worse, this is a natural consequence of mobility. Yet these same devices are often used to transmit confidential data.
Fortunately, Ethernet security standards already exist. Let’s take a closer look at what’s available and examine the technology advances that will enable them to readily secure networked IoT communications.
All Call AAA
The OSI protocol stack can host security protocols at various levels. Due to regulations like PCI, HIPAA, Sarbanes-Oxley, and Basel II that mandate strict data confidentiality, applications may run their own security protocols with application- and layer-specific encryption. SSH and HTTPS, which operate at Layer 4 (L4) and above in the OSI stack, are two such examples. IPSec (operating at Layer 3, or L3) is typical in routed networks. In Ethernet networks, however, which operate at Layer 2 (L2), IEEE 802.1AE MACsec is the standard encryption protocol (see “The Skinny on IPsec vs. MACsec”).
As the IIoT standardizes on Ethernet for networked communications, L2 encryption becomes an ideal solution. The reason is simple—there’s a direct relationship between the OSI layer at which security is implemented and the security solution’s strength. Securing at a lower layer means more robust protection.
Still, encryption is just one aspect of security, only covering data confidentiality. It does not, for example, prevent unauthorized access on a trusted network by a hacker spoofing a “trusted” device. To prevent such intrusions, it’s imperative to authenticate, authorize, and account (AAA) for devices and networks, as well as applications. This is arguably even more essential than application-layer security.
While AAA is commonplace for the applications layer, these principles are less uniformly enforced for the network and device/link layer. The latter may be especially vulnerable, since rogue devices could be swapped with network elements outside of physically secured areas and gain access to an entire network. Without securing the network and device/link layer, application-level security is largely in vain.
The other critical piece to Ethernet security is the IEEE 802.1x KeySec protocol. When used with a Remote Authentication Dial-In User Service (RADIUS) authentication server, KeySec can deliver the AAA capabilities needed to secure Ethernet communications.
Through a combination of IEEE 802.1AE and IEEE 802.1X, Ethernet can readily handle numerous security requirements, such as:
• AAA: This establishes the origin of any secure data transmitted in the network (using IEEE 802.1x and a RADIUS authentication server).
• Data integrity: The MACsec Integrity Check Value Field (ICV) safeguards against data replacement, modification, or delay beyond specific bounds. The ICV reflects changes when an Ethernet payload is tampered with—if it fails to match what was sent, the traffic is dropped.
• Data confidentiality: Using IEEE 802.1AE MACsec AES encryption (128- or 256-bit) ensures that only intended parties can read secured data.
Support for strong 256-bit, as well as 128-bit, encryption will be imperative for IoT devices. We already see this requirement emerging—the IEEE 802.1AEbn standard centers on enhanced confidentiality using 256-bit encryption. Notably, certain government agencies, such as the U.S. National Security Agency, already mandate compliance with this standard.
The Basics of MACsec
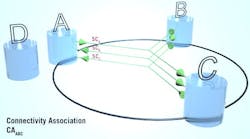
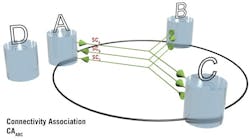
MACsec generates a secure Connectivity Association (CA) between two or more trusted Hosts. Within each CA, security is guaranteed. A MACsec instance, or Security Entity (SecY), exists in each Host for every CA. Multiple CAs are needed for network-wide security.
Figure 1 shows a secure CA between the three Hosts, A, B, and C. Host D is not part of CAABC, but can communicate without security with the other Hosts.
Each CA Host creates a Secure Channel (SC) between itself and the other CA Hosts, with each SC using one Secure Association Key (SAK) to encrypt data. At any given point in time, only one Secure Association (SA) resides on an SC. SAKs are updated regularly, allowing each SC up to four SAKs for present and future use. The SA is a long-lived relationship between Hosts, whereas the SA is short-lived, existing only as long as a particular SAK is in use.
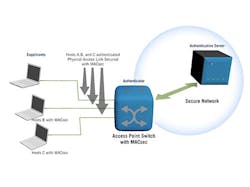
MACsec is designed for use with the port-based access-control protocols of IEEE 802.1XTM, which includes the Extensible Authentication Protocol over LAN (EAPOL) and MACsec Key Agreement protocol (MKA, or KeySec). EAPOL is used to authenticate the credentials of the subscriber and allows the subscriber access to the network. It works in conjunction with AAA protocols such as RADIUS (Fig. 2). Once the subscriber is authenticated, MKA enables the confidentiality and integrity features available with MACsec.
2. MACsec is designed for use with IEEE 802.1XTMâs port-based access-control protocols, including the Extensible Authentication Protocol over LAN (EAPOL) and MACsec Key Agreement protocol (MKA, or KeySec). EAPOL, which helps authenticate the credentials of the subscriber and allows the subscriber access to the network, works with AAA protocols such as RADIUS, shown in this diagram.
Going With The Flow: The New Face of MACsec
So if L2 security is the best for Ethernet communications, why haven’t we seen it more widely used in wide-area networks (WANs)? IEEE 802.1AE MACsec, as originally designed, encrypts network traffic on a link-by-link basis. This approach limited its practical use anywhere other than data centers and local-area networks. However, recent technology advances address this limitation, paving the path for widespread use of L2 security in the WAN.
A modern tag- and flow-based implementation of the MACsec standard from Vitesse Semiconductor incorporates several key innovations:
• VLAN headers or MPLS tags of Ethernet packets are left unencrypted, or “in the clear.” As a result, L2-encrypted data is able to be routed and switched normally through third-party networks that can remain unaware that the data is even encrypted. A significant benefit is that devices can also be remotely authenticated over unsecured third-party networks. This will be vital for IoT devices, which may often connect over third-party networks with varied trust levels.
• Connection flows, rather than entire WAN-facing ports, are encrypted. Therefore, multiple virtual connections out of a single port can be individually encrypted, providing far more granularity and flexibility to manage secured service delivery.
• IEEE 1588 network timing is preserved in conjunction with line-rate 256-bit AES encryption. Encryption and timing accuracy are traditionally incompatible. By definition, encryption increases packet size to add the extra information about the encryption. This introduces variable delays up to the 200-ns range, which can wreak havoc on wireless network timing. Such a scenario becomes particularly important as mobility figures more prominently in the IoT.
These technology advances make MACsec well-suited to secure WAN networks, especially as Ethernet becomes ubiquitous in all network types.
Conclusion
The IoT is quickly reshaping our world and the way in which we communicate to each other and to things. Ethernet will play a significant role in that transformation as it becomes the standard communications protocol in these emerging networks. However, strong security will be essential for applications, devices, and networks in order to realize the tremendous economic and productivity benefits made possible by connecting more systems to each other and the cloud. With security a chief concern, the good news is that silicon and software solutions incorporating recent technology advances in IEEE 802.1AE MACsec and IEEE 802.1x KeySec are readily available to protect our network communications. Taking that next step is up to us.