The Embedded Systems Conference was a bit smaller this year, but traffic around the booths was heavier and the tech sessions were as good as in the past. Overall, it was a good show.
Of course, the Internet of Things (IoT) was on everyone’s lips, highlighted in most of the tech sessions and hyped on the floor. One big question was: What does it mean to secure the Internet of Things (IoT)? Everyone agrees that security is paramount, only second to connectivity in importance. Unfortunately IoT security is about as nebulous as defining what IoT is.
On the plus side, discussions about things like root of trust and secure boot have gone from blank faces to checklist items. Issues like Heartbleed (see “What Heartbleed Should Teach Embedded Programmers”) as well as a host of other attacks, viruses, and Trojans has at least made developers more wary. It has also made them more aware of at least some of the tools beyond firewalls and simple encryption. I suspect there are even those who do not disable SELinux at the first sign of security errors.
End-to-end security as well as security in depth (see “Home Security Defense in Depth”) will be needed to secure IoT environments. Companies like Green Hills Software and Wind River need to take the lead in delivering solutions since they have been dealing with these issues and providing tools and support for quite a while—although it has often been for more specialized application areas such as avionics and military. We cannot simply ignore these issues just because a sports band seems like an innocuous device.
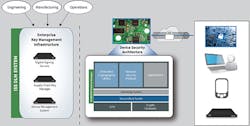
One part of the equation is key management. This used to be simple when keys were used for things like Web servers or email, but the game changes when we are talking about millions of IoT devices from a single source. Green Hills’ INTEGRITY Security Services (ISS) has been doing this as part of a consulting service, but it has also released an Embedded Cryptographic Toolkit (ECT) that delivers end-to-end key management (Fig. 1).
It is part of a Device Lifecycle Management (DLM) System that is an enterprise key management infrastructure. The enterprise is another space that has held security at a higher level within the development process. ECT targets the manufacturing and management of cryptographic support for IoT devices.
ECT allows applications to communicate securely without trusting the network. It can help ensure that software is not tampered with and it can help encrypt critical data. It can also address remote software updates.
Like the other security components, it is only part of the whole that is necessary. I still do not see a more integrated approach being taken in the delivery of security solutions. For example, vendors need to at least have module options that address every aspect of an IoT environment from secure boot to securing updates of the operating system and applications. It will be the only way for the average developer to easily incorporate security into the application, and it needs to be done at the start of development. Whitelisting, firewalls, and encryption are only pieces that need to be integrated.