Sonata: An Open-Source CHERIoT-Ibex Evaluation Platform
What you’ll learn:
- Some of the ways CHERIoT significantly reduces the attack surface for common vulnerabilities.
- How the Sonata platform helps embedded engineers evaluate a full CHERIoT-Ibex system ahead of silicon availability in a cost- and time-efficient manner.
- How Sonata also empowers developers to create their own enhancements to the CHERIoT ecosystem (both hardware and software).
With data and intellectual property being so valuable for businesses today, protecting these assets from theft or compromise is of utmost importance. As a result, embedded-systems engineers (whether in mobile, IoT, or OT) are always seeking to leverage the most up-to-date, effective cybersecurity technologies available.
It’s no wonder, then, given CHERI’s effectiveness in squashing memory-related vulnerabilities, there’s strong demand for a low-cost CHERIoT-Ibex evaluation platform that has minimal barriers to entry.
Evaluating CHERI Using the Sonata Platform
The Sonata platform, part of the UK Research and Innovation’s (UKRI) Digital Security by Design (DSbD)-funded Sunburst project, is an open-source initiative designed to offer exactly that—an easy on-ramp into the CHERI ecosystem for evaluators.
Sonata is the first FPGA prototyping/evaluation platform designed to run the CHERIoT-Ibex core. It includes an FPGA-based printed circuit board (PCB) with extensive connectivity, the complete RTL design (and loadable bitstream) for a CHERIoT-Ibex system-on-chip (SoC) that the FPGA can host, along with firmware, software, and documentation to make the whole package fly.
The CHERIoT technology was developed by Microsoft, based on the CHERI (Capability Hardware Enhanced RISC Instructions) work done by the University of Cambridge and SRI International. Microsoft’s First Steps in CHERIoT Security Research blog details how CHERIoT addresses potential security issues.
Embedded systems and IoT ecosystems are typically “built upon a diverse set of codebases written in C/C++ (mostly C), usually with zero mitigations in place, due to real or perceived overheads. This means that there are a lot of memory safety vulnerabilities that are easily exploited,” according to Microsoft.
At the core of Sonata’s memory safety guarantees is the CHERIoT instruction set with its CHERI capabilities that enforce fine-grained least-privilege access to memory. The compiler and operating system can leverage capabilities to ensure software only has access to the memory it needs with the minimal privileges required to perform its function. This eliminates a large number of vulnerabilities, such as buffer overflows (which often facilitate code injection attacks).
The Sunburst project (of which Sonata is a part) has plans to go beyond FPGA, too. This past November, lowRISC and SCI Semiconductor announced a drive to tapeout a CHERIoT-Ibex microcontroller SoC to help move the CHERI technology toward commercial adoption.
The collaboration is focused on creating a new open-source top-level design—with publicly available design verification (DV) dashboards—built around the same CHERIoT-Ibex core deployed on Sonata. It will support the innovation required for the creation of a commercially available device from SCI Semiconductor within its advanced ICENI device family, targeting a wide array of OT applications.
Oxford University Innovation Ltd. will also be contributing to the project, providing additional confidence in the robustness of the CHERIoT-Ibex design through formal verification.
Sonata Deep Dive
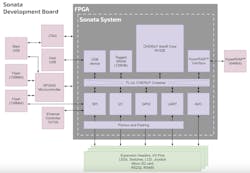
The figure shows the main components of the Sonata PCB and how they interact with the CHERIoT-Ibex SoC RTL running on the FPGA.
Sonata is intended to be used by academics and commercial developers who are interested in exploring CHERI for embedded, OT, and IoT use cases. Because its software, RTL, and PCB design are all open source, users have maximum flexibility in how they engage.
- First, using the pre-provided bitstream, they can treat Sonata as a (capability-aware) software development platform with excellent hardware connectivity and debugging support.
- Second, engineers interested in the CHERIoT-Ibex core itself can modify its open-source RTL design (adding support for custom instructions, for example) and then rapidly evaluate those changes on a FPGA.
- Third, although Sonata’s PCB already has great connectivity options and is modestly priced, its design is open. Thus, developers can spin their own PCB, for example, to support particular interfacing requirements.
To make Sonata accessible to the widest possible audience, the team opted to utilize a cost-effective FPGA, the Xilinx Artix 7. Balancing affordability with performance, this device can fully support the peripherals on the board and have sufficient performance for many embedded use cases. Its widespread support of development tools further enhances its appeal.
The Sonata system also has some tricks up its sleeve. For example, it offers HyperRAM as an alternative to DRAM, which offers similar performance without the need for a DDR controller. Currently, 1 MB of HyperRAM is accessible, all of which have associated capability tags (stored in 16 kB of SRAM).
Another advanced function is the CHERIoT hardware revocation engine, integrated from the cheriot-safe repository. In CHERIoT-Ibex, when memory is freed, its revocation “shadow” bits are set. Therefore, should an attempt be made to load a capability referencing such memory, it’s automatically invalidated.
However, the revocation engine can be programmed to scan specific memory areas in the background and revoke capabilities pointing to deallocated memory, even if those capabilities aren’t being actively loaded. As a result, this memory can be reused without risking unintended access by old capabilities.
Sonata Software
On the software side, a full build of Microsoft's CHERIoT RTOS is provided for Sonata, with driver support for Sonata peripherals integrated from the software repository. A flash bootloader enables easy “drag and drop” programming, where a generated UF2 file is copied to Sonata’s virtual USB drive (in a similar manner to the RP2040 and Arm Mbed platforms). Environment setup and build instructions are available for Windows, macOS, and Linux.
There are, in total, three ways to program the board’s software:
- You can use the flash storage on the Sonata board. This doesn’t require special tools and allows for an image to come online automatically at boot.
- You can use OpenOCD to program the image onto RAM and then run this image. This is typically employed during development.
- You can “splice” the software into the FPGA image. It provides a single “bitstream” that includes both hardware definition and software. This can be helpful for making system images that come alive as soon as possible after boot.
Simplifying Security Implementation via Sonata
Sonata is part of the wider Sunburst project, whose purpose is to improve the security of embedded devices through increased adoption of secure hardware. In that context, Sonata’s contribution is to provide an easy, fully open-source way for embedded systems engineers to start working with and evaluating the CHERIoT-Ibex core (and CHERI technology more generally), initiating development efforts on FPGAs now but with a straightforward migration path once SoC silicon is ready.
There’s no need to wait to experience the power of capabilities for yourself—evaluation units of the Sonata PCB are currently available for purchase from Mouser Electronics.
About the Author

Gavin Ferris
CEO, lowRISC
Dr. Gavin Ferris is a technologist and serial entrepreneur. Following his early career at DreamWorks SKG, he co-founded a number of startups, including the DSP/digital radio company RadioScape and fintech business Crescent Technology. When the latter was acquired by Aspect Capital, a multi-billion-dollar systematic hedge fund manager, Dr. Ferris became its chief architect and, ultimately, chief investment officer (CIO).
After leaving Aspect, Gavin co-founded lowRISC C.I.C., the non-profit host of the OpenTitan project, where he currently serves as pro bono CEO; he is also a co-founder and director of the CHERI Alliance C.I.C... Gavin holds a computer science degree and a Ph.D. in AI from Cambridge University.