Imagination Technologies' latest MIPS core, the M15xx, is designed to be secure and tamperproof. The M15xx is part of the Series5 Warrior family that include the Imagination Technologies P5600 announced last year.
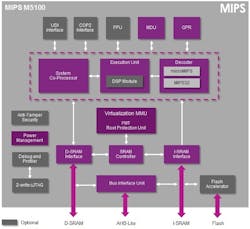
The latest incarnation addresses the low end of the 32-bit compute spectrum and is based on the microAptiv architecture (see MIPS Aptiv Family Brings Consolidation And Raises Performance Bar). The M5100 is the microcontroller implementation (Fig. 1). It is designed for on-chip SRAM and lacks the caching found in the M5150. The M5100 provides a more deterministic platform.
Related Articles
- MIPS Aptiv Family Brings Consolidation And Raises Performance Bar
- High Performance 32-bit Microcontroller Delivers 330 DMIPS
The tamper resistant design addresses IP protection as well as application security . The anti-tamper features two pseudo random number generators , injection of random pipeline stalls and even user defined scrambling of RAM and SPRAM data/addresses. This obfuscation makes the system harder to attack but it is the other features that are designed to limit the determined hacker.
Even the debug feature is protected. It can also be disabled using a one-time disable fuse or via software. This requires the proper keys in addition to following a multistage lock/unlock sequence.
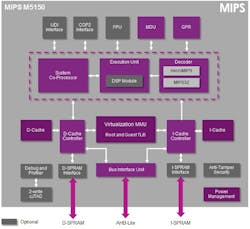
The M5150 is the microprocessor version (Fig. 2). It includes data and instruction cache and controllers and shares the tamper resistant design of the M5100.
The M51xx microAptiv base is built around a 5-stage pipeline with 32 general purpose registers. The architecture can deliver 3.4 Coremark/MHz and 1.57 DMIPS/MHz. The DSP and SIMD engine has over 150 instructions including 70 SIMD and 38 multiply/accumulate (MAC) instructions . The system is designed to minimize interrupt latency necessary for demanding real time applications.
Both cores can decode the microMIPS and MIPS32 instruction set. Optional logic includes the DSP, floating point unit (FPU), and universal debugging interface (UDI). They support the COP2 coprocessor interface.
The architecture supports hardware virtualization . Imagination provides two open source hypervisors. This includes Linux KVM that is a Type II hypervisor and Fiasco-OC that is an L4 kernel Type I hypervisor. Third party hypervisors are also available.
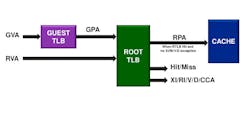
The M5150 has the more robust virtualization support (Fig. 3). It utilizes a conventional translation lookaside buffer (TLB) architecture.
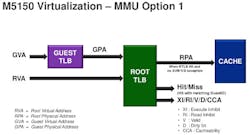
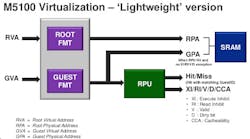
The M5100 virtualization support is more limited (Fig. 4). It has a Root Protection Unit (RPU) instead of a TLB. This provides isolation and limited address mapping but not on the same order as what the M5150 is capable of
The M5100 and M5150 target similar but different application spaces. The M5100 addresses applications that are fixed while the M5150 application space tends to be more dynamic. Both can benefit from the other features including the tamper protection.