Securing Data in the Quantum Era
This article is part of TechXchange: Quantum Computing and Security.
What you’ll learn:
- Coupled with the incredible pace of growth in quantum computing are challenges pertaining to federal, enterprise, and personal data security.
- Transitioning from classical to quantum computers is a global endeavor, with organizations around the world laying out their own "post quantum computing" recommendations as well.
Quantum computers are moving closer to tackling challenges where traditional computers fall short. In 2021, the quantum computing market size was valued at around U.S.$457.9 million and is expected to reach around $5.3 billion by 2030, according to Zion Market Research.
With the potential to perform faster calculations, work on multiple computations simultaneously, and utilize interconnected quantum bits (entangled qubits), the rise of accessible quantum computing will be advantageous across industries—from finance and banking to healthcare to transportation. From an artificial intelligence/machine learning (AI/ML) perspective, quantum computers will have the ability to solve optimization problems, analyze large datasets, simulate quantum systems for AI use cases, and so much more.
However, with new technological milestones come new threats the industry must learn to combat. Quantum computers are no different. As companies race to reach the quantum finish line, serious security implications come into focus. It’s time to start considering what the future of security may look like with quantum computers in the picture and determine how to advance cryptography standards accordingly.
A Leap Forward for Computing, a Step Back for Security
Governments, researchers, and tech leaders around the globe have warned that quantum computers will eventually be able to break the asymmetric encryption used today, putting critical communication and data protected with existing hardware and software at risk.
While quantum computers are still in the development stages, the U.S. National Institute of Standards and Technology (NIST) noted in January this year that by 2029, there’s a one in five chance some fundamental public key cryptography will be broken.
Some of the most widely adopted security algorithms, such as elliptic-curve cryptography (ECC) and Rivest-Shamir-Adleman (RSA), used to safeguard sensitive electronic data like bank account information and medical records can be compromised in the quantum era. All modern security protocols, including TLS, IPsec, MACsec, and DTLS, rely on ECC and RSA for their key exchanges and are therefore at risk.
Classic asymmetric cryptographic methods for key exchange and digital signatures will quickly become vulnerable once powerful-enough quantum computers exist. This is because quantum computers leveraging appropriate algorithms, like Shor’s, could accelerate the extraction of the corresponding private key from a publicly accessible key. Thus, any data encrypted using the public key can be decrypted without authorization.
AI/ML often deals with sensitive data, including personal information, confidential business assets, financial transactions, and more. If an adversary were able to break the key encryption used in an AI/ML system, not only would they gain unauthorized access to sensitive data, but they could manipulate ML models or impersonate authorized users.
Quantum computers leverage Shor’s algorithm, reducing the security of integer discrete logarithms, including ECC and RSA. This makes it so no reasonable key size would effectively secure data. General symmetric cryptography, as well as Advanced Encryption Standard (AES), Secure Hash Algorithm 2 (SHA-2), and SHA-3, will likely experience a relatively smaller security decrease due to quantum computers.
To reap the full benefits of quantum computers and avoid consequences when they do hit the market, security solutions must be developed and implemented simultaneously.
The Quantum Secure Transition
Numerous efforts have been initiated to create and implement novel cryptography algorithms able to replace RSA and ECC while evading both classical and quantum attacks. This is known as “post-quantum cryptography” (PQC).
NIST has been central to developing and standardizing PQC algorithms in the U.S. In July of 2022, they announced the first group of algorithms designed to defend against a quantum attack. CRYSTALS-Kyber was chosen as a Key Encapsulation Mechanism (KEM) and CRYSTALS-Dilithium, FALCON, and SPHINCS+ as digital signature algorithms. The NIST post-quantum cryptographic standard is expected to be finalized over the next few years, integrating the four encryption standards selected.
Soon after the algorithm selection, the U.S. National Security Agency (NSA) released “CNSA 2.0,” an update to its Commercial National Security Algorithm Suite (CNSA) mandating the utilization of CRYSTALS-Kyber and CRYSTALS-Dilithium as quantum-resistant algorithms. For firmware protection, NIST and NSA recommend stateful hash-based algorithms such as eXtended Merkle Signature Scheme (XMSS) or Leighton-Micali Signatures (LMS).
These updates provide a recommended timeline for the U.S. government and related suppliers to adopt these new PQC algorithms before data is vulnerable to quantum attacks.
Given the speed at which modern encryption standards may become obsolete, the NSA requires all National Security Systems (NSS) to transition to PQC software and firmware signing now, prefer its use by 2025, and complete this transition by 2030. Networking equipment should support and prefer CNSA 2.0 by 2026, and exclusively use CNSA 2.0 by 2030. A full transition to PQC algorithms by legacy equipment should be completed by 2033.
What to Expect Next
Transitioning from classical to quantum computers is a global endeavor, with organizations around the world laying out their own PQC recommendations as well. Europe’s guidelines, for example, are closely aligned with NIST’s, but Frodo KEM and Classic McEliece KEM algorithms are also accepted.
While a timeline for the standardization of more algorithms has yet to be solidified, it’s plausible that soon, international organizations like the Internet Research Task Force’s (IRTF) Crypto Forum Research Group, the Internet Engineering Task Force (IETF), and the International Organization for Standardization/International Electrotechnical Commission (ISO/IEC) will begin to approve additional algorithms. And they will integrate these into the RFCs and specifications for the secure communication protocols, such as TLS, IPsec, MACsec, etc.
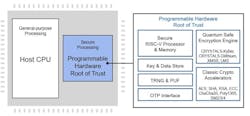
Chip manufacturers have already started preparing for the “Quantum Secure Transition,” expanding security IP offerings with Quantum Safe cryptographic solutions for future-proof data center and communications security. One way these organizations are taking strides toward quantum security is with next-gen hardware solutions that use NIST and CNSA quantum-resistant algorithms to secure hardware and data. These can include standalone acceleration hardware, or more advanced root-of-trust technology (see figure).
With these offerings, applications requiring the highest level of security, such as data centers, AI, and ML, will be able to transition away from traditional cryptography for encryption and begin preparing to fight quantum attacks of the future.
Conclusion
Quantum computing has long been a concept of science fiction, often depicted in pop culture and entertainment as a futuristic development changing the world as we know it. But as it gains momentum across industry, government, and academia, it won’t be long before we transition from the testing stages to deployment.
While the industry works to safeguard data from quantum threats with PQC, it’s up to enterprises to inventory systems for applications that use public-key cryptography and create a game plan for transitioning to new cryptography standards before future quantum threats become vital.
Read more articles in the TechXchange: Quantum Computing and Security.
About the Author

Gijs Willemse
Senior Director of Product Management, Security IP, Rambus
Gijs Willemse is senior director of product management for Rambus Security. Gijs has been working in the Security IP business for over 18 years. In various roles, he has always engaged directly with many of the Tier-1 SoC manufacturers, securing their assets and protecting their products from vulnerabilities in the field. His roots are in the high-speed networking IPs deployed in modern data centers and 5G networks. With Rambus, its security IPs, small footprint consumer devices to high-end/high-speed server products, are secured through their complete lifecycle.
Gijs has a Master’s degree in electrical engineering (Information Technology) from the Technical University in Eindhoven and holds several patents.