New ARM v8 Architecture for Microcontrollers
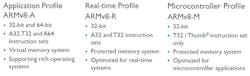
ARM’s TrustZone security has been key to its higher-end solutions like the Cortex-A series, but it is now part of the Cortex-M with the advent of the ARMv8-M microcontroller architecture (Fig. 1). The microcontroller version was announced at this year’s ARM TechCon conference in Santa Clara, Calif. The ARMv8-M architecture will prove very useful for the Internet of Things (IoT).
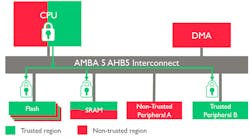
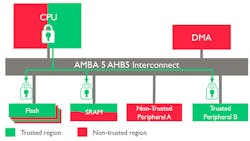
The ARMv8-M microcontroller architecture implements the 32-bit T32/Thumb instruction set. This remains intact, but now incorporates trusted hardware in the form of a protected memory and I/O systems built around TrustZone technology (Fig. 2). This includes hardware cryptography support and a true random number generator (TRNG) as well as secure boot support.
The new architecture differs from the higher-end platforms because it is designed to provide low, deterministic latency support. It also does not provide hypervisor support found in platforms like the Cortex-A because that would also incur overhead that microcontroller applications cannot afford either in timing or hardware overhead.
The ARMv8-M architecture does provide access limits on memory, both flash and RAM, as well as access controls on peripherals and debug support. The TrustZone support also addresses firmware IP protection and secure remote firmware updates. The new AMBA 5 AHB5 specification includes support for TrustZone peripherals making it easy to build secure SoCs with custom peripherals.
Support by the third-party community includes all major Cortex-M supporters, including operating system and tool companies like Green Hills Software, Micrium, Express Logic, Mentor Graphics, IAR Systems, Symantec, Trustonic, Segger, and FreeRTOS.
The implications of the ARMv8-M architecture for IoT are significant. It provides a common security architecture that will be adopted by the wide array of Cortex-M vendors. It is scalable from the Cortex-M0 to the Cortex-M7 (see “Cortex-M7 Contains Configurable Tightly Coupled Memory”). This will make it easier for developers to target the microcontroller space that has included a variety of proprietary security measures.