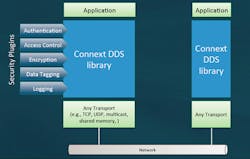
Real-Time Innovations’ (RTI) Connext DDS Secure brings policy-based security to the Data Distribution Service (DDS). RTI’s Connext DDS has been used in applications that span embedded to enterprise applications (see “Data Distribution Service Scales From Embedded To The Enterprise”). The latest version implements a plug-in oriented architecture that provides policy-based security that scales across this range (Fig. 1).
The current set of plug-ins includes:
- Authentication
- Access control
- Encryption
- Data tagging
- Logging
The plug-in approach allows developers to enhance plug-ins as well as providing ones that can take advantage of resident hardware and software. For example, the encryption plug-in can utilize hardware accelerated encryption support. Encryption can applied at the field level significantly reducing encryption overhead if only some data requires high security.
The access control provides the XML policy-based support. It is scalable so it can work on low end, embedded hardware where more sophisticated access control is not required. Nodes communicating directly with each other require matching access control support. Access control can be fine grained so access to a particular field can be controlled.
DDS provides a publish/subscribe environment (see “DDS V1.0 Standardizes Publish/Subscribe”). Connext DDS allows the environment to incorporate the cloud through Internet of Things (IoT) devices. Data can flow from a publisher through the network to any number of subscribers based on their needs. It handles quality of service, replication and a host of other features that make the data transfers and communication links transparent to applications. Connext DDS is compliant with the Open Management Group’s (OMG) DDS specification.
This file type includes high resolution graphics and schematics when applicable.
Data tagging allows meta data to be added to DDS data. This can be used to enhance access control. For example, access to a particular piece of data may be limited by an application. Added meta data allows the application to determine what policy to apply.
The Connext DDS support is already modular so it can provide more limited support on low end, embedded clients as well as more sophisticated support on more powerful platforms. It does not have a single point of failure and can deal with a range of communication networks and protocols. It can utilize low bandwidth, limited connectivity links as well as manage high speed networks with multicast support.
Connext DDS can be used for DDS applications without modification. Policies can be applied at a level above applications or applications can take more control over their security using Connext DDS interfaces. It can be tailored to support legacy applications that may utilize other communication methods.
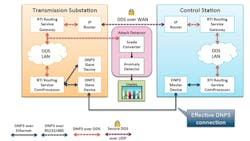
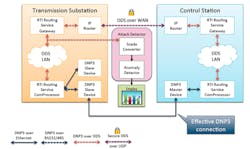
Pacific Northwest National Laboratory (PNNL) worked with RTI to provide a better, more secure communication system for their Supervisory Control and Data Acquisition (SCADA ) applications (Fig. 2). SCADA is used in a variety of industrial control systems like those used by electric utilities.
In this instance, PNNL had a SCADA system that used the standard Distributed Network Protocol 3 (DNP3). Unfortunately, DNP3 is not very secure and it is point-to-point. This can make security and reliable communication more difficult.
RTI and PNNL created a DNP3 routing service interface. This allowed the SCADA applications to use Connext DDS’ communication system that can be more secure as well as more reliable. Policies can be used to control access to the SCADA data that now flows only through Connext DDS.
The implementation has the added advantage of providing access to the SCADA data via DDS in addition to replacing the DNP3 support that the system was intended to secure.
Connext DDS Secure can be used in any Connext DDS environment to improve overall security. Connext DDS Secure and Connext DDS work with most operating systems such as Windows, Linux, Android, iOS and many RTOS systems.
About the Author
William G. Wong
Senior Content Director - Electronic Design and Microwaves & RF
I am Editor of Electronic Design focusing on embedded, software, and systems. As Senior Content Director, I also manage Microwaves & RF and I work with a great team of editors to provide engineers, programmers, developers and technical managers with interesting and useful articles and videos on a regular basis. Check out our free newsletters to see the latest content.
You can send press releases for new products for possible coverage on the website. I am also interested in receiving contributed articles for publishing on our website. Use our template and send to me along with a signed release form.
Check out my blog, AltEmbedded on Electronic Design, as well as his latest articles on this site that are listed below.
You can visit my social media via these links:
- AltEmbedded on Electronic Design
- Bill Wong on Facebook
- @AltEmbedded on Twitter
- Bill Wong on LinkedIn
I earned a Bachelor of Electrical Engineering at the Georgia Institute of Technology and a Masters in Computer Science from Rutgers University. I still do a bit of programming using everything from C and C++ to Rust and Ada/SPARK. I do a bit of PHP programming for Drupal websites. I have posted a few Drupal modules.
I still get a hand on software and electronic hardware. Some of this can be found on our Kit Close-Up video series. You can also see me on many of our TechXchange Talk videos. I am interested in a range of projects from robotics to artificial intelligence.